A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
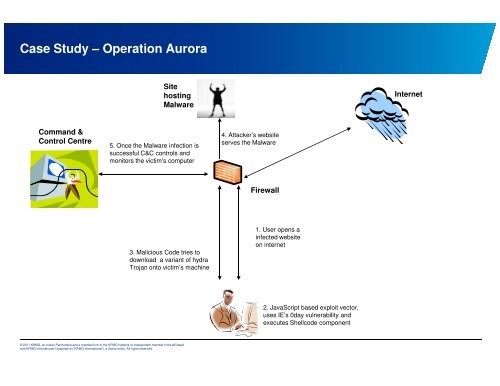
Case Study – Operati<strong>on</strong> Aurora<br />
Command &<br />
C<strong>on</strong>trol Centre<br />
Site<br />
hosting<br />
Malware<br />
5. Once the Malware infecti<strong>on</strong> is<br />
successful C&C c<strong>on</strong>trols and<br />
m<strong>on</strong>itors the victim's computer<br />
3. Malicious Code tries to<br />
download a variant of hydra<br />
Trojan <strong>on</strong>to victim’s machine<br />
© 2011 KPMG, an Indian Partnership and a member firm of the KPMG network of independent member firms affiliated<br />
with KPMG Internati<strong>on</strong>al Cooperative (“KPMG Internati<strong>on</strong>al”), a Swiss entity. All rights reserved.<br />
4. Attacker’s website<br />
serves the Malware<br />
Firewall<br />
1. User opens a<br />
infected website<br />
<strong>on</strong> internet<br />
2. JavaScript based exploit vector,<br />
uses IE’s 0day vulnerability and<br />
executes Shellcode comp<strong>on</strong>ent<br />
Internet