What is eToken Enterprise? - tlk
What is eToken Enterprise? - tlk
What is eToken Enterprise? - tlk
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
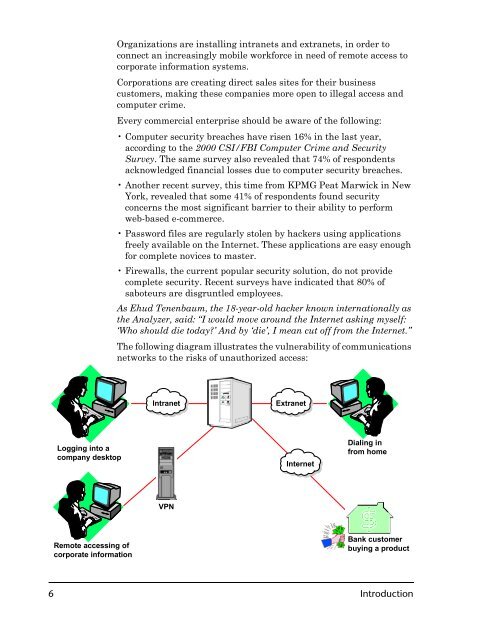
Logging into a<br />
company desktop<br />
Remote accessing of<br />
corporate information<br />
Organizations are installing intranets and extranets, in order to<br />
connect an increasingly mobile workforce in need of remote access to<br />
corporate information systems.<br />
Corporations are creating direct sales sites for their business<br />
customers, making these companies more open to illegal access and<br />
computer crime.<br />
Every commercial enterpr<strong>is</strong>e should be aware of the following:<br />
Computer security breaches have r<strong>is</strong>en 16% in the last year,<br />
according to the 2000 CSI/FBI Computer Crime and Security<br />
Survey. The same survey also revealed that 74% of respondents<br />
acknowledged financial losses due to computer security breaches.<br />
Another recent survey, th<strong>is</strong> time from KPMG Peat Marwick in New<br />
York, revealed that some 41% of respondents found security<br />
concerns the most significant barrier to their ability to perform<br />
web-based e-commerce.<br />
Password files are regularly stolen by hackers using applications<br />
freely available on the Internet. These applications are easy enough<br />
for complete novices to master.<br />
Firewalls, the current popular security solution, do not provide<br />
complete security. Recent surveys have indicated that 80% of<br />
saboteurs are d<strong>is</strong>gruntled employees.<br />
As Ehud Tenenbaum, the 18-year-old hacker known internationally as<br />
the Analyzer, said: “I would move around the Internet asking myself:<br />
‘Who should die today?’ And by ‘die’, I mean cut off from the Internet.”<br />
The following diagram illustrates the vulnerability of communications<br />
networks to the r<strong>is</strong>ks of unauthorized access:<br />
Intranet Extranet<br />
VPN<br />
Internet<br />
Dialing in<br />
from home<br />
Bank customer<br />
buying a product<br />
6 Introduction