1 - Acta Technica Corviniensis
1 - Acta Technica Corviniensis
1 - Acta Technica Corviniensis
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
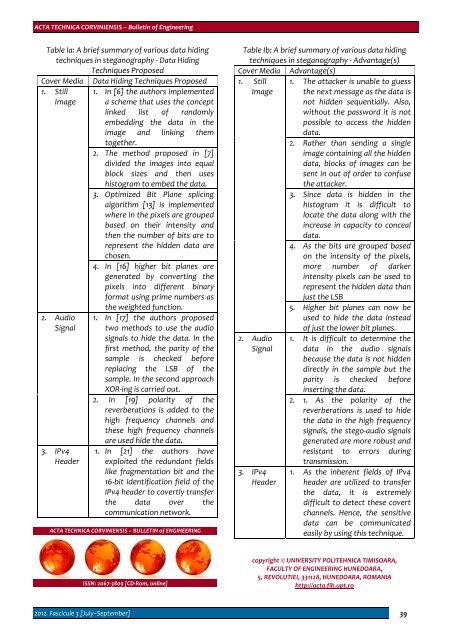
ACTA TECHNICA CORVINIENSIS – Bulletin of EngineeringTable Ia: A brief summary of various data hidingtechniques in steganography ‐ Data HidingTechniques ProposedCover Media1. StillImage2. AudioSignal3. IPv4HeaderData Hiding Techniques Proposed1. In [6] the authors implementeda scheme that uses the conceptlinked list of randomlyembedding the data in theimage and linking themtogether.2. The method proposed in [7]divided the images into equalblock sizes and then useshistogram to embed the data.3. Optimized Bit Plane splicingalgorithm [13] is implementedwhere in the pixels are groupedbased on their intensity andthen the number of bits are torepresent the hidden data arechosen.4. In [16] higher bit planes aregenerated by converting thepixels into different binaryformat using prime numbers asthe weighted function.1. In [17] the authors proposedtwo methods to use the audiosignals to hide the data. In thefirst method, the parity of thesample is checked beforereplacing the LSB of thesample. In the second approachXOR‐ing is carried out.2. In [19] polarity of thereverberations is added to thehigh frequency channels andthese high frequency channelsare used hide the data.1. In [21] the authors haveexploited the redundant fieldslike fragmentation bit and the16‐bit identification field of theIPv4 header to covertly transferthe data over thecommunication network.ACTA TECHNICA CORVINIENSIS – BULLETIN of ENGINEERINGTable Ib: A brief summary of various data hidingtechniques in steganography ‐ Advantage(s)Cover Media Advantage(s)1. StillImage1. The attacker is unable to guessthe next message as the data isnot hidden sequentially. Also,without the password it is notpossible to access the hiddendata.2. Rather than sending a singleimage containing all the hiddendata, blocks of images can besent in out of order to confusethe attacker.3. Since data is hidden in thehistogram it is difficult tolocate the data along with theincrease in capacity to concealdata.4. As the bits are grouped basedon the intensity of the pixels,more number of darkerintensity pixels can be used torepresent the hidden data thanjust the LSB2. AudioSignal3. IPv4Header5. Higher bit planes can now beused to hide the data insteadof just the lower bit planes.1. It is difficult to determine thedata in the audio signalsbecause the data is not hiddendirectly in the sample but theparity is checked beforeinserting the data.2. 1. As the polarity of thereverberations is used to hidethe data in the high frequencysignals, the stego‐audio signalsgenerated are more robust andresistant to errors duringtransmission.1. As the inherent fields of IPv4header are utilized to transferthe data, it is extremelydifficult to detect these covertchannels. Hence, the sensitivedata can be communicatedeasily by using this technique.ISSN: 2067‐3809 [CD‐Rom, online]copyright © UNIVERSITY POLITEHNICA TIMISOARA,FACULTY OF ENGINEERING HUNEDOARA,5, REVOLUTIEI, 331128, HUNEDOARA, ROMANIAhttp://acta.fih.upt.ro2012. Fascicule 3 [July–September] 39