BATTLEFIELD DIGITAL FORENSICS
BDF_Battlefield_Digital_Forensics_final
BDF_Battlefield_Digital_Forensics_final
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
In a wireless ad-hoc network, all the nodes are interconnected by single-hop or multi-hop wireless connections.<br />
There is no centralised control or base station to coordinate the behaviour of each node in the network. As a<br />
result, each node must be self-configurable in order to adapt to various network topologies. Nodes can assist in<br />
transmitting packets from a source to a destination through wireless connections in a fully peer-to-peer<br />
fashion. At the same time, because of the wireless connections, service coverage and bandwidth availability<br />
become critical issues in the wireless channels.<br />
A main feature of ad-hoc networks is that all the nodes in the network have the freedom to move around,<br />
which causes the network topology to change dynamically and unpredictably.<br />
Mobile ad-hoc networks that include specific gateway nodes towards other networks (such as cellular, satellite,<br />
or WiMAX) can be called hybrid mobile ad-hoc networks [8]. Some ad-hoc network routing protocols provide<br />
delay-tolerant (or disruption-tolerant) networking (DTN), and this could be used to create an ad-hoc mobile file<br />
system. DTN works over existing protocol stacks in various network architectures and provides a store-andforward<br />
functionality [9]. One use case for DTN is military battlegrounds where the disconnection may be<br />
caused by mobility of vehicles, forces and devices, environmental factors, intentional electronic jamming done<br />
by the enemy, or by the loss of the acquisition vector. DTN can be considered as one technique used in<br />
opportunistic networks. Opportunistic networking is more flexible than DTN, because opportunistic networks<br />
may also contain other communication techniques than protocols used in the internet, and each single node<br />
acts as a gateway 5 [10].<br />
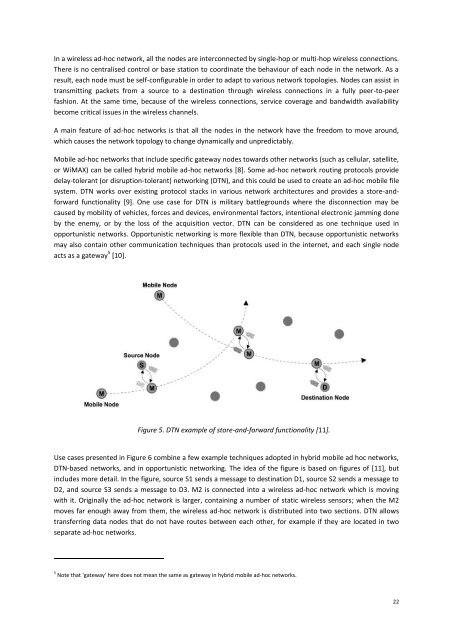
Figure 5. DTN example of store-and-forward functionality [11].<br />
Use cases presented in Figure 6 combine a few example techniques adopted in hybrid mobile ad hoc networks,<br />
DTN-based networks, and in opportunistic networking. The idea of the figure is based on figures of [11], but<br />
includes more detail. In the figure, source S1 sends a message to destination D1, source S2 sends a message to<br />
D2, and source S3 sends a message to D3. M2 is connected into a wireless ad-hoc network which is moving<br />
with it. Originally the ad-hoc network is larger, containing a number of static wireless sensors; when the M2<br />
moves far enough away from them, the wireless ad-hoc network is distributed into two sections. DTN allows<br />
transferring data nodes that do not have routes between each other, for example if they are located in two<br />
separate ad-hoc networks.<br />
5 Note that ‘gateway’ here does not mean the same as gateway in hybrid mobile ad-hoc networks.<br />
22