BATTLEFIELD DIGITAL FORENSICS
BDF_Battlefield_Digital_Forensics_final
BDF_Battlefield_Digital_Forensics_final
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
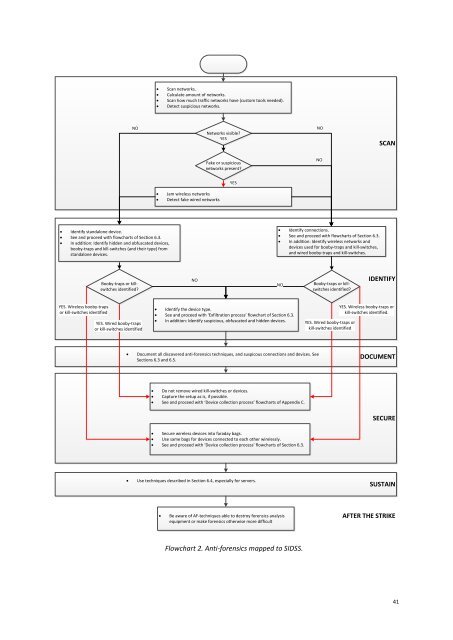
Scan networks.<br />
Calculate amount of networks.<br />
Scan how much traffic networks have (custom tools needed).<br />
Detect suspicious networks.<br />
NO<br />
Networks visible?<br />
YES<br />
NO<br />
SCAN<br />
Fake or suspicious<br />
networks present?<br />
NO<br />
YES<br />
<br />
<br />
Jam wireless networks<br />
Detect fake wired networks<br />
Identify standalone device.<br />
See and proceed with flowcharts of Section 6.3.<br />
In addition: Identify hidden and obfuscated devices,<br />
booby-traps and kill-switches (and their type) from<br />
standalone devices.<br />
Identify connections.<br />
See and proceed with flowcharts of Section 6.3.<br />
In addition: Identify wireless networks and<br />
devices used for booby-traps and kill-switches,<br />
and wired booby-traps and kill-switches.<br />
Booby-traps or killswitches<br />
identified?<br />
NO<br />
NO<br />
Booby-traps or killswitches<br />
identified?<br />
IDENTIFY<br />
YES. Wireless booby-traps<br />
or kill-switches identified<br />
YES. Wired booby-traps<br />
or kill-switches identified<br />
Identify the device type.<br />
See and proceed with ‘Exfiltration process’ flowchart of Section 6.3.<br />
In addition: Identify suspicious, obfuscated and hidden devices.<br />
YES. Wired booby-traps or<br />
kill-switches identified<br />
YES. Wireless booby-traps or<br />
kill-switches identified.<br />
<br />
Document all discovered anti-forensics techniques, and suspicous connections and devices. See<br />
Sections 6.3 and 6.5.<br />
DOCUMENT<br />
Do not remove wired kill-switches or devices.<br />
Capture the setup as is, if possible.<br />
See and proceed with ‘Device collection process’ flowcharts of Appendix C.<br />
SECURE<br />
Secure wireless devices into faraday bags.<br />
Use same bags for devices connected to each other wirelessly.<br />
See and proceed with ‘Device collection process’ flowcharts of Section 6.3.<br />
<br />
Use techniques described in Section 6.4, especially for servers.<br />
SUSTAIN<br />
<br />
Be aware of AF-techniques able to destroy forensics analysis<br />
equipment or make forensics otherwise more difficult<br />
AFTER THE STRIKE<br />
Flowchart 2. Anti-forensics mapped to SIDSS.<br />
41