BATTLEFIELD DIGITAL FORENSICS
BDF_Battlefield_Digital_Forensics_final
BDF_Battlefield_Digital_Forensics_final
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
8<br />
Exfiltration Solutions<br />
Michal Sadlon<br />
Exfiltration is one of the most difficult parts of the forensics process and covers activities over the entire<br />
triaging model. Exfiltration does not only consist of acquisition: there are also other important operations that<br />
should be done throughout. As mentioned in Chapter 6 – ‘Computer Forensics‘, there are several aspects<br />
leading to different scenarios.<br />
8.1 Exfiltration Process<br />
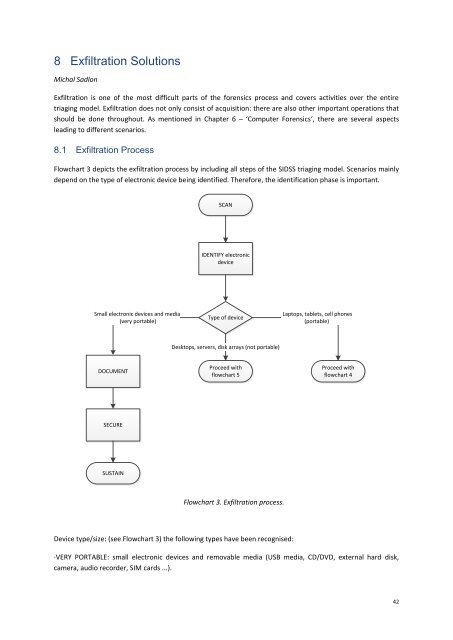
Flowchart 3 depicts the exfiltration process by including all steps of the SIDSS triaging model. Scenarios mainly<br />
depend on the type of electronic device being identified. Therefore, the identification phase is important.<br />
SCAN<br />
IDENTIFY electronic<br />
device<br />
Small electronic devices and media<br />
(very portable)<br />
Type of device<br />
Laptops, tablets, cell phones<br />
(portable)<br />
Desktops, servers, disk arrays (not portable)<br />
DOCUMENT<br />
Proceed with<br />
flowchart 5<br />
Proceed with<br />
flowchart 4<br />
SECURE<br />
SUSTAIN<br />
Flowchart 3. Exfiltration process.<br />
Device type/size: (see Flowchart 3) the following types have been recognised:<br />
·VERY PORTABLE: small electronic devices and removable media (USB media, CD/DVD, external hard disk,<br />
camera, audio recorder, SIM cards ...).<br />
42