BATTLEFIELD DIGITAL FORENSICS
BDF_Battlefield_Digital_Forensics_final
BDF_Battlefield_Digital_Forensics_final
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Mobile destination<br />
node #3 (human)<br />
D3<br />
M3<br />
Mobile node #2<br />
(tank) with a moving<br />
wireless ad hoc<br />
network<br />
M2<br />
Wireless ad hoc<br />
network #3 Source node #3<br />
(part of wireless<br />
ad hoc network)<br />
S3<br />
M1 carries<br />
message for D3 for<br />
nothing<br />
S3 -> M2: message for D3<br />
M1<br />
D3M3 moves away from the<br />
original location too early<br />
D3<br />
M3<br />
Mobile node #4<br />
(helicopter)<br />
M4<br />
D3M3 combines with M4<br />
Moving wireless ad<br />
hoc network #3.2<br />
When M2 goes far enough,<br />
wireless ad hoc network #3<br />
is cut into two networks<br />
(#3.1 and #3.2).<br />
Destination node<br />
#1<br />
(part of wireless<br />
ad hoc network)<br />
D1<br />
M2<br />
Wireless ad hoc<br />
network #2<br />
M1 -> GW -> D1: message for D1<br />
GW<br />
M1<br />
M1<br />
M2<br />
M1 -> M2: message going to D2<br />
M2 -> M2: message going to D3<br />
(however without discarding it locally)<br />
M2 -> SS: messages for D2 and D3<br />
D3M3 and M4<br />
are combined<br />
M4<br />
D3<br />
M3<br />
M2<br />
SS<br />
Static<br />
data storage<br />
station<br />
SS -> M4 and D3M3: message for D3<br />
SS -> M4 and D3M3: message for D2<br />
M1<br />
S2 -> GW -> M1: message going to D2<br />
GW<br />
Wireless ad hoc<br />
network #1<br />
Source node #1<br />
S1<br />
Message for D2<br />
M1<br />
S1 -> M2: message going to D1<br />
Source node #2<br />
(part of wireless<br />
ad hoc network)<br />
S2<br />
D3M3 and M4 separate<br />
M1<br />
Mobile node #1<br />
(droid)<br />
D3 -> D2: message going to D2<br />
D3<br />
M3<br />
M4<br />
Destination node #2<br />
D2<br />
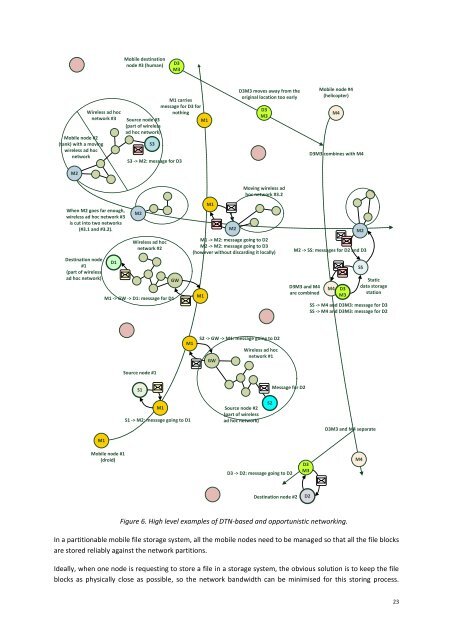
Figure 6. High level examples of DTN-based and opportunistic networking.<br />
In a partitionable mobile file storage system, all the mobile nodes need to be managed so that all the file blocks<br />
are stored reliably against the network partitions.<br />
Ideally, when one node is requesting to store a file in a storage system, the obvious solution is to keep the file<br />
blocks as physically close as possible, so the network bandwidth can be minimised for this storing process.<br />
23