BATTLEFIELD DIGITAL FORENSICS
BDF_Battlefield_Digital_Forensics_final
BDF_Battlefield_Digital_Forensics_final
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Recommendation: Be aware that harmless-looking devices may actually include several important devices<br />
containing possible evidences (scan and identify).<br />
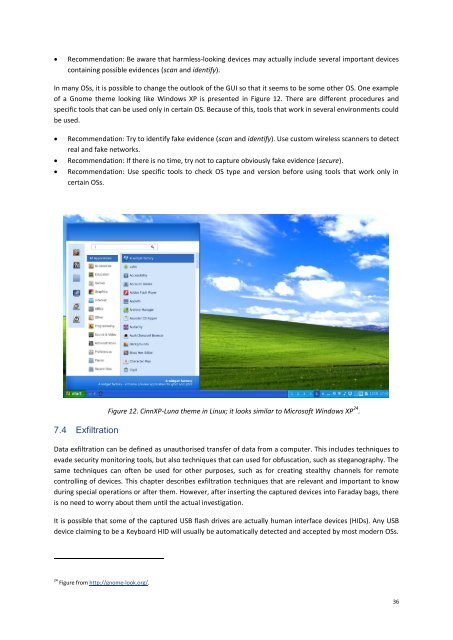
In many OSs, it is possible to change the outlook of the GUI so that it seems to be some other OS. One example<br />
of a Gnome theme looking like Windows XP is presented in Figure 12. There are different procedures and<br />
specific tools that can be used only in certain OS. Because of this, tools that work in several environments could<br />
be used.<br />
<br />
<br />
<br />
Recommendation: Try to identify fake evidence (scan and identify). Use custom wireless scanners to detect<br />
real and fake networks.<br />
Recommendation: If there is no time, try not to capture obviously fake evidence (secure).<br />
Recommendation: Use specific tools to check OS type and version before using tools that work only in<br />
certain OSs.<br />
7.4 Exfiltration<br />
Figure 12. CinnXP-Luna theme in Linux; it looks similar to Microsoft Windows XP 24 .<br />
Data exfiltration can be defined as unauthorised transfer of data from a computer. This includes techniques to<br />
evade security monitoring tools, but also techniques that can used for obfuscation, such as steganography. The<br />
same techniques can often be used for other purposes, such as for creating stealthy channels for remote<br />
controlling of devices. This chapter describes exfiltration techniques that are relevant and important to know<br />
during special operations or after them. However, after inserting the captured devices into Faraday bags, there<br />
is no need to worry about them until the actual investigation.<br />
It is possible that some of the captured USB flash drives are actually human interface devices (HIDs). Any USB<br />
device claiming to be a Keyboard HID will usually be automatically detected and accepted by most modern OSs.<br />
24 Figure from http://gnome-look.org/.<br />
36