proceedings of Student Mobility and ICT: Can E-LEARNING
proceedings of Student Mobility and ICT: Can E-LEARNING
proceedings of Student Mobility and ICT: Can E-LEARNING
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
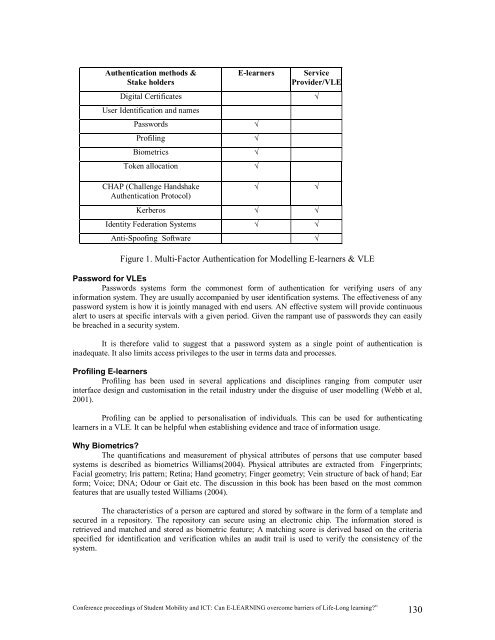
Authentication methods &<br />
Stake holders<br />
E-learners Service<br />
Provider/VLE<br />
Digital Certificates <br />
User Identification <strong>and</strong> names<br />
Passwords <br />
Pr<strong>of</strong>iling <br />
Biometrics <br />
Token allocation <br />
CHAP (Challenge H<strong>and</strong>shake<br />
Authentication Protocol)<br />
<br />
Kerberos <br />
Identity Federation Systems <br />
Anti-Spo<strong>of</strong>ing S<strong>of</strong>tware <br />
Figure 1. Multi-Factor Authentication for Modelling E-learners & VLE<br />
Password for VLEs<br />
Passwords systems form the commonest form <strong>of</strong> authentication for verifying users <strong>of</strong> any<br />
information system. They are usually accompanied by user identification systems. The effectiveness <strong>of</strong> any<br />
password system is how it is jointly managed with end users. AN effective system will provide continuous<br />
alert to users at specific intervals with a given period. Given the rampant use <strong>of</strong> passwords they can easily<br />
be breached in a security system.<br />
It is therefore valid to suggest that a password system as a single point <strong>of</strong> authentication is<br />
inadequate. It also limits access privileges to the user in terms data <strong>and</strong> processes.<br />
Pr<strong>of</strong>iling E-learners<br />
Pr<strong>of</strong>iling has been used in several applications <strong>and</strong> disciplines ranging from computer user<br />
interface design <strong>and</strong> customisation in the retail industry under the disguise <strong>of</strong> user modelling (Webb et al,<br />
2001).<br />
Pr<strong>of</strong>iling can be applied to personalisation <strong>of</strong> individuals. This can be used for authenticating<br />
learners in a VLE. It can be helpful when establishing evidence <strong>and</strong> trace <strong>of</strong> information usage.<br />
Why Biometrics?<br />
The quantifications <strong>and</strong> measurement <strong>of</strong> physical attributes <strong>of</strong> persons that use computer based<br />
systems is described as biometrics Williams(2004). Physical attributes are extracted from Fingerprints;<br />
Facial geometry; Iris pattern; Retina; H<strong>and</strong> geometry; Finger geometry; Vein structure <strong>of</strong> back <strong>of</strong> h<strong>and</strong>; Ear<br />
form; Voice; DNA; Odour or Gait etc. The discussion in this book has been based on the most common<br />
features that are usually tested Williams (2004).<br />
The characteristics <strong>of</strong> a person are captured <strong>and</strong> stored by s<strong>of</strong>tware in the form <strong>of</strong> a template <strong>and</strong><br />
secured in a repository. The repository can secure using an electronic chip. The information stored is<br />
retrieved <strong>and</strong> matched <strong>and</strong> stored as biometric feature; A matching score is derived based on the criteria<br />
specified for identification <strong>and</strong> verification whiles an audit trail is used to verify the consistency <strong>of</strong> the<br />
system.<br />
Conference <strong>proceedings</strong> <strong>of</strong> <strong>Student</strong> <strong>Mobility</strong> <strong>and</strong> <strong>ICT</strong>: <strong>Can</strong> E-<strong>LEARNING</strong> overcome barriers <strong>of</strong> Life-Long learning?” 130