PDF - Department of the Treasury
PDF - Department of the Treasury
PDF - Department of the Treasury
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
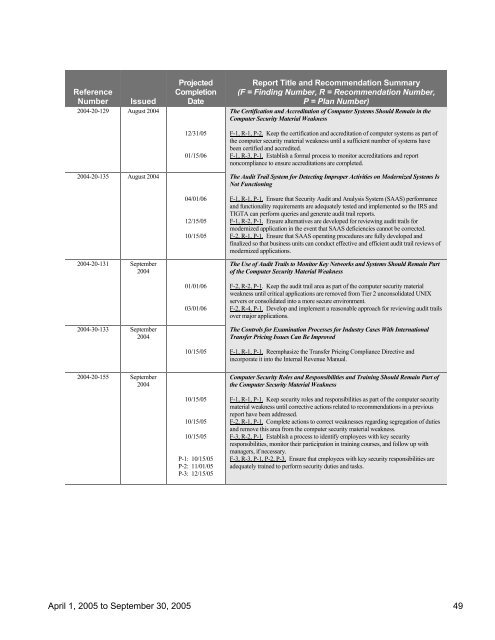
Reference<br />
Number<br />
Issued<br />
2004-20-129 August 2004<br />
2004-20-135 August 2004<br />
2004-20-131 September<br />
2004<br />
2004-30-133 September<br />
2004<br />
2004-20-155 September<br />
2004<br />
Projected<br />
Completion<br />
Date<br />
12/31/05<br />
01/15/06<br />
04/01/06<br />
12/15/05<br />
10/15/05<br />
01/01/06<br />
03/01/06<br />
10/15/05<br />
10/15/05<br />
10/15/05<br />
10/15/05<br />
P-1: 10/15/05<br />
P-2: 11/01/05<br />
P-3: 12/15/05<br />
Report Title and Recommendation Summary<br />
(F = Finding Number, R = Recommendation Number,<br />
P = Plan Number)<br />
The Certification and Accreditation <strong>of</strong> Computer Systems Should Remain in <strong>the</strong><br />
Computer Security Material Weakness<br />
F-1, R-1, P-2. Keep <strong>the</strong> certification and accreditation <strong>of</strong> computer systems as part <strong>of</strong><br />
<strong>the</strong> computer security material weakness until a sufficient number <strong>of</strong> systems have<br />
been certified and accredited.<br />
F-1, R-3, P-1. Establish a formal process to monitor accreditations and report<br />
noncompliance to ensure accreditations are completed.<br />
The Audit Trail System for Detecting Improper Activities on Modernized Systems Is<br />
Not Functioning<br />
F-1, R-1, P-1. Ensure that Security Audit and Analysis System (SAAS) performance<br />
and functionality requirements are adequately tested and implemented so <strong>the</strong> IRS and<br />
TIGTA can perform queries and generate audit trail reports.<br />
F-1, R-2, P-1. Ensure alternatives are developed for reviewing audit trails for<br />
modernized application in <strong>the</strong> event that SAAS deficiencies cannot be corrected.<br />
F-2, R-1, P-1. Ensure that SAAS operating procedures are fully developed and<br />
finalized so that business units can conduct effective and efficient audit trail reviews <strong>of</strong><br />
modernized applications.<br />
The Use <strong>of</strong> Audit Trails to Monitor Key Networks and Systems Should Remain Part<br />
<strong>of</strong> <strong>the</strong> Computer Security Material Weakness<br />
F-2, R-2, P-1. Keep <strong>the</strong> audit trail area as part <strong>of</strong> <strong>the</strong> computer security material<br />
weakness until critical applications are removed from Tier 2 unconsolidated UNIX<br />
servers or consolidated into a more secure environment.<br />
F-2, R-4, P-1. Develop and implement a reasonable approach for reviewing audit trails<br />
over major applications.<br />
The Controls for Examination Processes for Industry Cases With International<br />
Transfer Pricing Issues Can Be Improved<br />
F-1, R-1, P-1. Reemphasize <strong>the</strong> Transfer Pricing Compliance Directive and<br />
incorporate it into <strong>the</strong> Internal Revenue Manual.<br />
Computer Security Roles and Responsibilities and Training Should Remain Part <strong>of</strong><br />
<strong>the</strong> Computer Security Material Weakness<br />
F-1, R-1, P-1. Keep security roles and responsibilities as part <strong>of</strong> <strong>the</strong> computer security<br />
material weakness until corrective actions related to recommendations in a previous<br />
report have been addressed.<br />
F-2, R-1, P-1. Complete actions to correct weaknesses regarding segregation <strong>of</strong> duties<br />
and remove this area from <strong>the</strong> computer security material weakness.<br />
F-3, R-2, P-1. Establish a process to identify employees with key security<br />
responsibilities, monitor <strong>the</strong>ir participation in training courses, and follow up with<br />
managers, if necessary.<br />
F-3, R-3, P-1, P-2, P-3. Ensure that employees with key security responsibilities are<br />
adequately trained to perform security duties and tasks.<br />
April 1, 2005 to September 30, 2005 49