- Page 2:
WIRELESS SENSOR NETWORKS Technology
- Page 6 and 7:
WIRELESS SENSOR NETWORKS Technology
- Page 8 and 9:
CONTENTS Preface xi About the Autho
- Page 10 and 11:
CONTENTS vii 5.4 MAC Protocols for
- Page 12:
CONTENTS ix 9.3 Traditional Network
- Page 15 and 16:
xii PREFACE text provides thorough
- Page 17 and 18:
xiv ABOUT THE AUTHORS communication
- Page 20 and 21:
1 INTRODUCTION AND OVERVIEW OF WIRE
- Page 22 and 23:
INTRODUCTION 3 in the wireless case
- Page 24 and 25:
INTRODUCTION 5 In this book we emph
- Page 26 and 27:
INTRODUCTION 7 and low-power-consum
- Page 28 and 29:
INTRODUCTION 9 1. The typical mode
- Page 30 and 31:
INTRODUCTION 11 Commercial applica
- Page 32 and 33:
BASIC OVERVIEW OF THE TECHNOLOGY 13
- Page 34 and 35:
BASIC OVERVIEW OF THE TECHNOLOGY 15
- Page 36 and 37:
BASIC OVERVIEW OF THE TECHNOLOGY 17
- Page 38 and 39:
BASIC OVERVIEW OF THE TECHNOLOGY 19
- Page 40 and 41:
BASIC OVERVIEW OF THE TECHNOLOGY 21
- Page 42 and 43:
BASIC OVERVIEW OF THE TECHNOLOGY 23
- Page 44 and 45:
BASIC OVERVIEW OF THE TECHNOLOGY 25
- Page 46 and 47:
BASIC OVERVIEW OF THE TECHNOLOGY 27
- Page 48 and 49:
BASIC OVERVIEW OF THE TECHNOLOGY 29
- Page 50 and 51:
REFERENCES 31 Standards As implied
- Page 52 and 53:
REFERENCES 33 [1.22] D. Minoli, W.
- Page 54 and 55:
REFERENCES 35 [1.58] S. Lindsey et
- Page 56 and 57:
REFERENCES 37 [1.89] J. M. Kahn et
- Page 58 and 59:
BACKGROUND 39 static routing over t
- Page 60 and 61:
BACKGROUND 41 The WNs have computat
- Page 62 and 63:
RANGE OF APPLICATIONS 43 TABLE 2.1
- Page 64 and 65:
RANGE OF APPLICATIONS 45 TABLE 2.1
- Page 66 and 67:
RANGE OF APPLICATIONS 47 TABLE 2.1
- Page 68 and 69:
RANGE OF APPLICATIONS 49 expect wit
- Page 70 and 71:
EXAMPLES OF CATEGORY 2 WSN APPLICAT
- Page 72 and 73:
EXAMPLES OF CATEGORY 2 WSN APPLICAT
- Page 74 and 75:
EXAMPLES OF CATEGORY 2 WSN APPLICAT
- Page 76 and 77:
EXAMPLES OF CATEGORY 2 WSN APPLICAT
- Page 78 and 79:
EXAMPLES OF CATEGORY 1 WSN APPLICAT
- Page 80 and 81:
EXAMPLES OF CATEGORY 1 WSN APPLICAT
- Page 82 and 83:
EXAMPLES OF CATEGORY 1 WSN APPLICAT
- Page 84 and 85:
EXAMPLES OF CATEGORY 1 WSN APPLICAT
- Page 86 and 87:
EXAMPLES OF CATEGORY 1 WSN APPLICAT
- Page 88 and 89:
ANOTHER TAXONOMY OF WSN TECHNOLOGY
- Page 90 and 91:
REFERENCES 71 In aggregating system
- Page 92 and 93:
REFERENCES 73 [2.25] ‘‘Short Di
- Page 94 and 95:
3 BASIC WIRELESS SENSOR TECHNOLOGY
- Page 96 and 97:
SENSOR NODE TECHNOLOGY 77 2. Detect
- Page 98 and 99:
SENSOR NODE TECHNOLOGY 79 Hardware
- Page 100 and 101:
Figure 3.3 Some of the networking p
- Page 102 and 103:
Very small (10 1 mm 3 ) Ultrasmall
- Page 104 and 105:
WN OPERATING ENVIRONMENT 85 TABLE 3
- Page 106 and 107:
WN TRENDS 87 aggregated, fused, and
- Page 108 and 109:
WN TRENDS 89 TABLE 3.4 Partial List
- Page 110 and 111:
REFERENCES 91 to those sensors so t
- Page 112 and 113:
4 WIRELESS TRANSMISSION TECHNOLOGY
- Page 114 and 115:
RADIO TECHNOLOGY PRIMER 95 Ionosphe
- Page 116 and 117:
RADIO TECHNOLOGY PRIMER 97 TABLE 4.
- Page 118 and 119:
RADIO TECHNOLOGY PRIMER 99 TABLE 4.
- Page 120 and 121:
RADIO TECHNOLOGY PRIMER 101 citizen
- Page 122 and 123:
AVAILABLE WIRELESS TECHNOLOGIES 103
- Page 124 and 125:
AVAILABLE WIRELESS TECHNOLOGIES 105
- Page 126 and 127:
AVAILABLE WIRELESS TECHNOLOGIES 107
- Page 128 and 129:
AVAILABLE WIRELESS TECHNOLOGIES 109
- Page 130 and 131:
AVAILABLE WIRELESS TECHNOLOGIES 111
- Page 132 and 133:
AVAILABLE WIRELESS TECHNOLOGIES 113
- Page 134 and 135:
AVAILABLE WIRELESS TECHNOLOGIES 115
- Page 136 and 137:
AVAILABLE WIRELESS TECHNOLOGIES 117
- Page 138 and 139:
AVAILABLE WIRELESS TECHNOLOGIES 119
- Page 140 and 141:
AVAILABLE WIRELESS TECHNOLOGIES 121
- Page 142 and 143:
AVAILABLE WIRELESS TECHNOLOGIES 123
- Page 144 and 145:
AVAILABLE WIRELESS TECHNOLOGIES 125
- Page 146 and 147:
AVAILABLE WIRELESS TECHNOLOGIES 127
- Page 148 and 149:
AVAILABLE WIRELESS TECHNOLOGIES 129
- Page 150 and 151:
APPENDIX A: MODULATION BASICS 131 s
- Page 152 and 153:
APPENDIX A: MODULATION BASICS 133 T
- Page 154 and 155:
APPENDIX A: MODULATION BASICS 135 T
- Page 156 and 157:
APPENDIX A: MODULATION BASICS 137 P
- Page 158 and 159:
REFERENCES 139 algorithm, although
- Page 160 and 161:
REFERENCES 141 [4.36] C. Berrou, A.
- Page 162 and 163:
BACKGROUND 143 therefore be shared
- Page 164 and 165:
FUNDAMENTALS OF MAC PROTOCOLS 145 T
- Page 166 and 167:
FUNDAMENTALS OF MAC PROTOCOLS 147 q
- Page 168 and 169:
FUNDAMENTALS OF MAC PROTOCOLS 149 T
- Page 170 and 171:
FUNDAMENTALS OF MAC PROTOCOLS 151 d
- Page 172 and 173:
FUNDAMENTALS OF MAC PROTOCOLS 153 w
- Page 174 and 175:
FUNDAMENTALS OF MAC PROTOCOLS 155 F
- Page 176 and 177:
FUNDAMENTALS OF MAC PROTOCOLS 157 A
- Page 178 and 179:
MAC PROTOCOLS FOR WSNs 159 A B C D
- Page 180 and 181:
MAC PROTOCOLS FOR WSNs 161 multihop
- Page 182 and 183:
MAC PROTOCOLS FOR WSNs 163 can be o
- Page 184 and 185:
MAC PROTOCOLS FOR WSNs 165 of nodes
- Page 186 and 187:
SENSOR-MAC CASE STUDY 167 services
- Page 188 and 189:
SENSOR-MAC CASE STUDY 169 Nodes are
- Page 190 and 191:
SENSOR-MAC CASE STUDY 171 to secure
- Page 192 and 193:
IEEE 802.15.4 LR-WPAN 173 Sender RT
- Page 194 and 195:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 196 and 197:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 198 and 199:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 200 and 201:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 202 and 203:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 204 and 205:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 206 and 207:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 208 and 209:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 210 and 211:
IEEE 802.15.4 LR-WPANs STANDARD CAS
- Page 212 and 213:
REFERENCES 193 residing within 30 f
- Page 214 and 215:
REFERENCES 195 [5.25] K. Sohrabi, J
- Page 216 and 217:
6 ROUTING PROTOCOLS FOR WIRELESS SE
- Page 218 and 219:
DATA DISSEMINATION AND GATHERING 19
- Page 220 and 221:
ROUTING CHALLENGES AND DESIGN ISSUE
- Page 222 and 223:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 224 and 225:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 226 and 227:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 228 and 229:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 230 and 231:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 232 and 233:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 234 and 235:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 236 and 237:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 238 and 239:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 240 and 241:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 242 and 243:
ROUTING STRATEGIES IN WIRELESS SENS
- Page 244 and 245:
REFERENCES 225 first two faces and
- Page 246 and 247:
REFERENCES 227 International Confer
- Page 248 and 249:
7 TRANSPORT CONTROL PROTOCOLS FOR W
- Page 250 and 251:
TRADITIONAL TRANSPORT CONTROL PROTO
- Page 252 and 253:
TRADITIONAL TRANSPORT CONTROL PROTO
- Page 254 and 255:
TRANSPORT PROTOCOL DESIGN ISSUES 23
- Page 256 and 257: EXAMPLES OF EXISTING TRANSPORT CONT
- Page 258 and 259: EXAMPLES OF EXISTING TRANSPORT CONT
- Page 260 and 261: PERFORMANCE OF TRANSPORT CONTROL PR
- Page 262 and 263: PERFORMANCE OF TRANSPORT CONTROL PR
- Page 264 and 265: REFERENCES 245 [7.2] Y. Sankarasubr
- Page 266 and 267: WSN MIDDLEWARE PRINCIPLES 247 are v
- Page 268 and 269: MIDDLEWARE ARCHITECTURE 249 TABLE 8
- Page 270 and 271: MIDDLEWARE ARCHITECTURE 251 for pos
- Page 272 and 273: EXISTING MIDDLEWARE 253 of sensor n
- Page 274 and 275: EXISTING MIDDLEWARE 255 reasonable
- Page 276 and 277: EXISTING MIDDLEWARE 257 tools and s
- Page 278 and 279: REFERENCES 259 8.5 CONCLUSION In th
- Page 280 and 281: REFERENCES 261 [8.24] S. Kim, S. H.
- Page 282 and 283: TRADITIONAL NETWORK MANAGEMENT MODE
- Page 284 and 285: NETWORK MANAGEMENT DESIGN ISSUES 26
- Page 286 and 287: EXAMPLE OF MANAGEMENT ARCHITECTURE:
- Page 288 and 289: OTHER ISSUES RELATED TO NETWORK MAN
- Page 290 and 291: REFERENCES 271 [9.2] L. B. Ruiz, F.
- Page 292 and 293: 10 OPERATING SYSTEMS FOR WIRELESS S
- Page 294 and 295: OPERATING SYSTEM DESIGN ISSUES 275
- Page 296 and 297: EXAMPLES OF OPERATING SYSTEMS 277 c
- Page 298 and 299: EXAMPLES OF OPERATING SYSTEMS 279 w
- Page 300 and 301: REFERENCES 281 10.3.9 PicOS One pro
- Page 302 and 303: 11 PERFORMANCE AND TRAFFIC MANAGEME
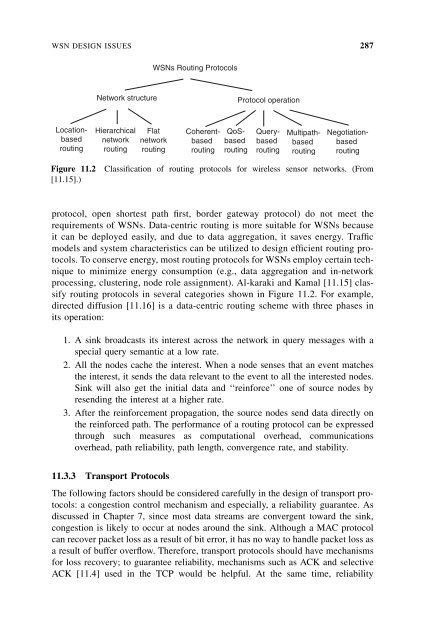
- Page 304 and 305: BACKGROUND 285 data relaying, and s
- Page 308 and 309: PERFORMANCE MODELING OF WSNs 289 du
- Page 310 and 311: PERFORMANCE MODELING OF WSNs 291 an
- Page 312 and 313: PERFORMANCE MODELING OF WSNs 293 Th
- Page 314 and 315: CASE STUDY: SIMPLE COMPUTATION OF T
- Page 316 and 317: CASE STUDY: SIMPLE COMPUTATION OF T
- Page 318 and 319: CASE STUDY: SIMPLE COMPUTATION OF T
- Page 320: REFERENCES 301 [11.12] I. Demirkol,
- Page 323 and 324: 304 INDEX Code-division multiple ac
- Page 325 and 326: 306 INDEX NEMS, 28 Network design,