Deze scriptie is geschreven door beide op persoonlijke titel
IT-control framework voor de Douanevereenvoudiging Self ... - Vurore
IT-control framework voor de Douanevereenvoudiging Self ... - Vurore
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
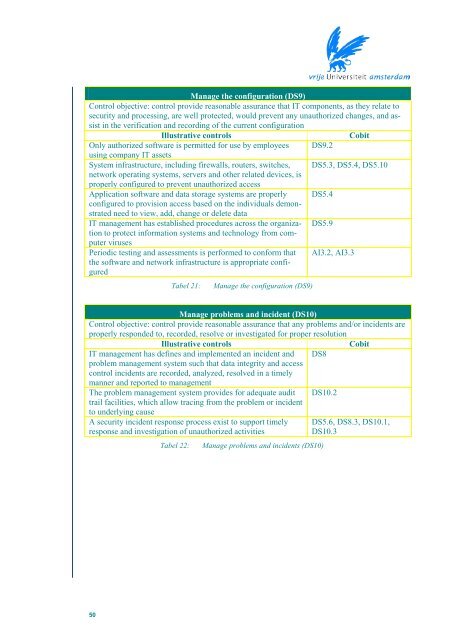
Manage the configuration (DS9)Control objective: control provide reasonable assurance that IT components, as they relate tosecurity and processing, are well protected, would prevent any unauthorized changes, and ass<strong>is</strong>tin the verification and recording of the current configurationIllustrative controlsCobitOnly authorized software <strong>is</strong> permitted for use by employees DS9.2using company IT assetsSystem infrastructure, including firewalls, routers, switches, DS5.3, DS5.4, DS5.10network <strong>op</strong>erating systems, servers and other related devices, <strong>is</strong>pr<strong>op</strong>erly configured to prevent unauthorized accessApplication software and data storage systems are pr<strong>op</strong>erly DS5.4configured to prov<strong>is</strong>ion access based on the individuals demonstratedneed to view, add, change or delete dataIT management has establ<strong>is</strong>hed procedures across the organizationto protect information systems and technology from com-DS5.9puter virusesPeriodic testing and assessments <strong>is</strong> performed to conform that AI3.2, AI3.3the software and network infrastructure <strong>is</strong> appr<strong>op</strong>riate configuredTabel 21:Manage the configuration (DS9)Manage problems and incident (DS10)Control objective: control provide reasonable assurance that any problems and/or incidents arepr<strong>op</strong>erly responded to, recorded, resolve or investigated for pr<strong>op</strong>er resolutionIllustrative controlsCobitIT management has defines and implemented an incident and DS8problem management system such that data integrity and accesscontrol incidents are recorded, analyzed, resolved in a timelymanner and reported to managementThe problem management system provides for adequate audit DS10.2trail facilities, which allow tracing from the problem or incidentto underlying causeA security incident response process ex<strong>is</strong>t to support timelyresponse and investigation of unauthorized activitiesTabel 22:Manage problems and incidents (DS10)DS5.6, DS8.3, DS10.1,DS10.350