Cyber Primer
AEWhbF
AEWhbF
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Cyber</strong> threats<br />
Case study 8 – Social engineering for the<br />
purpose of espionage<br />
These actions frequently take the form of phishing attacks or identity<br />
theft and are often aimed at social engineering, fraud or embarrassing the<br />
individual.<br />
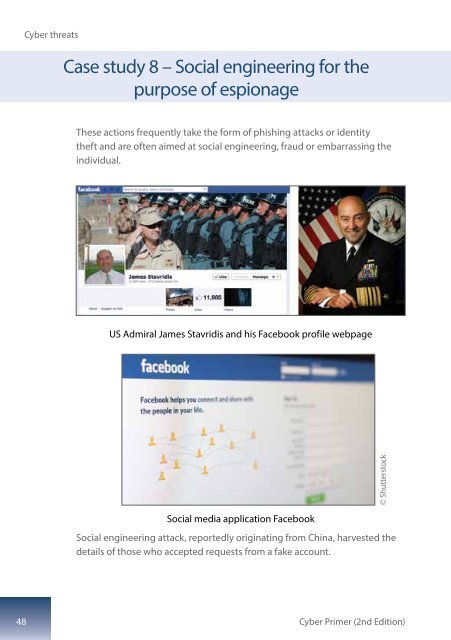
US Admiral James Stavridis and his Facebook profile webpage<br />
© Shutterstock<br />
Social media application Facebook<br />
Social engineering attack, reportedly originating from China, harvested the<br />
details of those who accepted requests from a fake account.<br />
48<br />
<strong>Cyber</strong> <strong>Primer</strong> (2nd Edition)