Cyber Primer
AEWhbF
AEWhbF
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Integrating cyber operations<br />
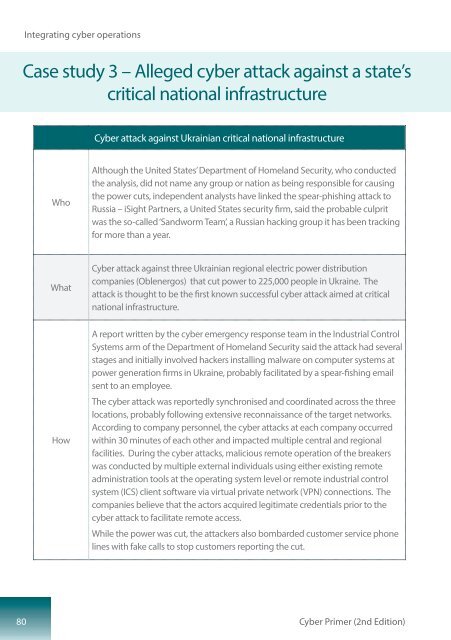
Case study 3 – Alleged cyber attack against a state’s<br />
critical national infrastructure<br />
<strong>Cyber</strong> attack against Ukrainian critical national infrastructure<br />
Who<br />
Although the United States’ Department of Homeland Security, who conducted<br />
the analysis, did not name any group or nation as being responsible for causing<br />
the power cuts, independent analysts have linked the spear-phishing attack to<br />
Russia – iSight Partners, a United States security firm, said the probable culprit<br />
was the so-called ‘Sandworm Team’, a Russian hacking group it has been tracking<br />
for more than a year.<br />
What<br />
<strong>Cyber</strong> attack against three Ukrainian regional electric power distribution<br />
companies (Oblenergos) that cut power to 225,000 people in Ukraine. The<br />
attack is thought to be the first known successful cyber attack aimed at critical<br />
national infrastructure.<br />
How<br />
A report written by the cyber emergency response team in the Industrial Control<br />
Systems arm of the Department of Homeland Security said the attack had several<br />
stages and initially involved hackers installing malware on computer systems at<br />
power generation firms in Ukraine, probably facilitated by a spear-fishing email<br />
sent to an employee.<br />
The cyber attack was reportedly synchronised and coordinated across the three<br />
locations, probably following extensive reconnaissance of the target networks.<br />
According to company personnel, the cyber attacks at each company occurred<br />
within 30 minutes of each other and impacted multiple central and regional<br />
facilities. During the cyber attacks, malicious remote operation of the breakers<br />
was conducted by multiple external individuals using either existing remote<br />
administration tools at the operating system level or remote industrial control<br />
system (ICS) client software via virtual private network (VPN) connections. The<br />
companies believe that the actors acquired legitimate credentials prior to the<br />
cyber attack to facilitate remote access.<br />
While the power was cut, the attackers also bombarded customer service phone<br />
lines with fake calls to stop customers reporting the cut.<br />
80<br />
<strong>Cyber</strong> <strong>Primer</strong> (2nd Edition)