Cyber Primer
AEWhbF
AEWhbF
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Cyber</strong> functions<br />
• command and control; and<br />
• effect achieved.<br />
3.12. The phases are not discrete events, instead they interact and overlap<br />
with each other and may vary in duration. They are equally applicable to the<br />
actions of a state or criminal. They are also dependent upon an attacker’s<br />
intent and availability of offensive cyber and intelligence capabilities. A<br />
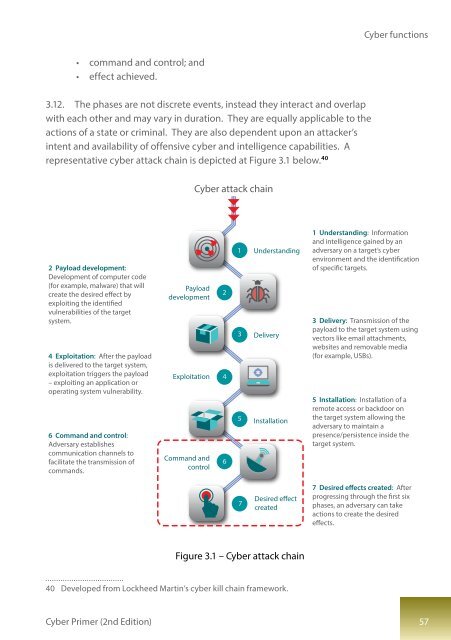
representative cyber attack chain is depicted at Figure 3.1 below. 40<br />
<strong>Cyber</strong> attack chain<br />
2 Payload development:<br />
Development of computer code<br />
(for example, malware) that will<br />
create the desired effect by<br />
exploiting the identified<br />
vulnerabilities of the target<br />
system.<br />
4 Exploitation: After the payload<br />
is delivered to the target system,<br />
exploitation triggers the payload<br />
– exploiting an application or<br />
operating system vulnerability.<br />
6 Command and control:<br />
Adversary establishes<br />
communication channels to<br />
facilitate the transmission of<br />
commands.<br />
Payload<br />
development<br />
Exploitation<br />
Command and<br />
control<br />
2<br />
4<br />
6<br />
1 Understanding<br />
3 Delivery<br />
5 Installation<br />
1 Understanding: Information<br />
and intelligence gained by an<br />
adversary on a target’s cyber<br />
environment and the identification<br />
of specific targets.<br />
3 Delivery: Transmission of the<br />
payload to the target system using<br />
vectors like email attachments,<br />
websites and removable media<br />
(for example, USBs).<br />
5 Installation: Installation of a<br />
remote access or backdoor on<br />
the target system allowing the<br />
adversary to maintain a<br />
presence/persistence inside the<br />
target system.<br />
7<br />
Desired effect<br />
created<br />
7 Desired effects created: After<br />
progressing through the first six<br />
phases, an adversary can take<br />
actions to create the desired<br />
effects.<br />
Figure 3.1 – <strong>Cyber</strong> attack chain<br />
40 Developed from Lockheed Martin’s cyber kill chain framework.<br />
<strong>Cyber</strong> <strong>Primer</strong> (2nd Edition) 57