Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
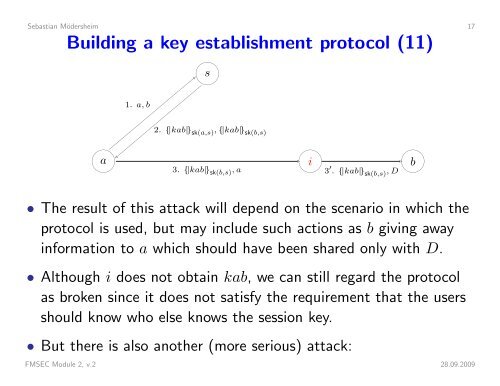
Sebastian Mödersheim 17Building a key establishment protocol (11)s 1. a, b2. {|kab|} sk(a,s) , {|kab|} sk(b,s) a3. {|kab|} sk(b,s) , a i3 ′ . {|kab|} sk(b,s) , D b• The result of this attack will depend on the scenario in which theprotocol is used, but may include such actions as b giving awayinformation to a which should have been shared only with D.• Although i does not obtain kab, we can still regard the protocolas broken since it does not satisfy the requirement that the usersshould know who else knows the session key.• But there is also another (more serious) attack:FMSEC Module 2, v.2 28.09.2009