Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
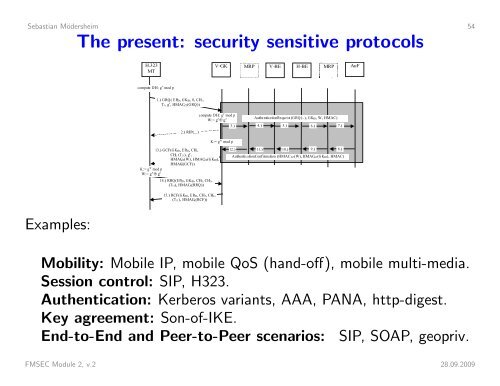
Sebastian Mödersheim 54The present: security sensitive protocolsH.323MTV−GK MRP V−BE H−BE MRP AuFcompute DH: g x mod p1.) GRQ( EPID, GKID, 0, CH1,T1, g x , HMACZZ(GRQ))2.) RIP(...)compute DH: g y mod pW:= g x ⊕ g y3.)AuthenticationRequest (GRQ(..), GKID, W, HMAC)4.) 5.) 6.) 7.)13.) GCF(GKID, EPID, CH1,CH2, (T13), g y ,HMACZZ(W), HMACZZ(GKID),HMACK(GCF))K:= g xy mod pW:= g x ⊕ g y14.) RRQ(EPID, GKID, CH2, CH3,(T14), HMACK(RRQ))15.) RCF(GKID, EPID, CH3, CH4,(T15), HMACK(RCF))K:= g xy mod p12.) 11.) 10.) 9.) 8.)AuthenticationConfirmation (HMAC ZZ(W), HMACZZ(GKID), HMAC)Examples:Mobility: Mobile IP, mobile QoS (hand-off), mobile multi-media.Session control: SIP, H323.Authentication: Kerberos variants, AAA, PANA, http-digest.Key agreement: Son-of-IKE.End-to-End and Peer-to-Peer scenarios: SIP, SOAP, geopriv.FMSEC Module 2, v.2 28.09.2009