Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
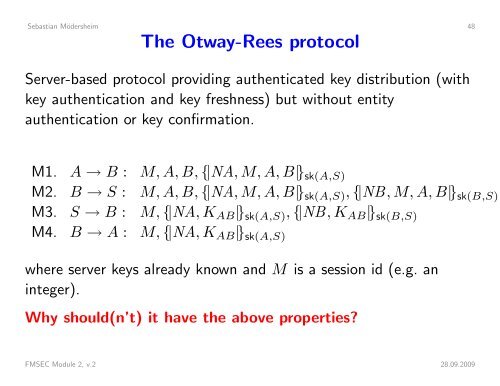
Sebastian Mödersheim 48The Otway-Rees protocolServer-based protocol providing authenticated key distribution (withkey authentication and key freshness) but without entityauthentication or key confirmation.M1. A → B : M, A, B, {|NA, M, A, B|} sk(A,S)M2. B → S : M, A, B, {|NA, M, A, B|} sk(A,S) , {|NB, M, A, B|} sk(B,S)M3. S → B : M, {|NA, K AB |} sk(A,S) , {|NB, K AB |} sk(B,S)M4. B → A : M, {|NA, K AB |} sk(A,S)where server keys already known and M is a session id (e.g. aninteger).Why should(n’t) it have the above properties?FMSEC Module 2, v.2 28.09.2009