Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
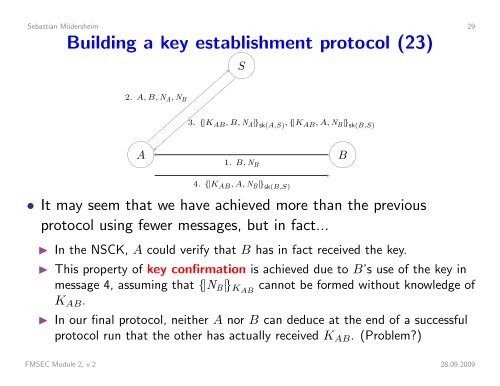
Sebastian Mödersheim 29Building a key establishment protocol (23)2. A, B, N A , N BS3. {|K AB , B, N A |} sk(A,S) , {|K AB , A, N B |} sk(B,S) A1. B, N B4. {|K AB , A, N B |} sk(B,S) B• It may seem that we have achieved more than the previousprotocol using fewer messages, but in fact...◮ In the NSCK, A could verify that B has in fact received the key.◮ This property of key confirmation is achieved due to B’s use of the key inmessage 4, assuming that {|N B |} KAB cannot be formed without knowledge ofK AB .◮ In our final protocol, neither A nor B can deduce at the end of a successfulprotocol run that the other has actually received K AB . (Problem?)FMSEC Module 2, v.2 28.09.2009