Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
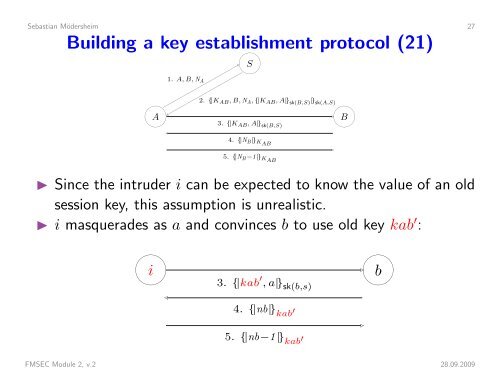
Sebastian Mödersheim 27Building a key establishment protocol (21)A1. A, B, N A S2. {|K AB , B, N A , {|K AB , A|} sk(B,S) |} sk(A,S)3. {|K AB , A|} sk(B,S) 4. {|N B |} KAB5. {|N B −1 |} KAB B◮ Since the intruder i can be expected to know the value of an oldsession key, this assumption is unrealistic.◮ i masquerades as a and convinces b to use old key kab ′ : i3. {|kab ′ , a|} sk(b,s) 4. {|nb|} kab ′ b 5. {|nb−1 |} kab ′FMSEC Module 2, v.2 28.09.2009