Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
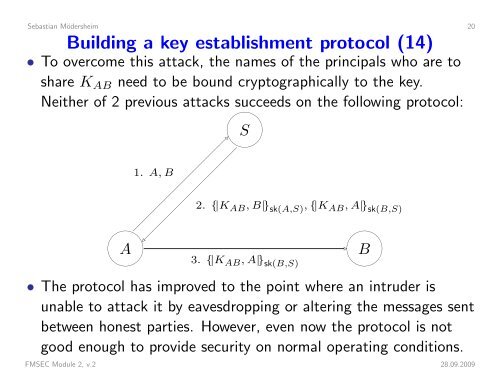
Sebastian Mödersheim 20Building a key establishment protocol (14)• To overcome this attack, the names of the principals who are toshare K AB need to be bound cryptographically to the key.Neither of 2 previous attacks succeeds on the following protocol:S1. A, B2. {|K AB , B|} sk(A,S) , {|K AB , A|} sk(B,S) AB 3. {|K AB , A|} sk(B,S)• The protocol has improved to the point where an intruder isunable to attack it by eavesdropping or altering the messages sentbetween honest parties. However, even now the protocol is notgood enough to provide security on normal operating conditions.FMSEC Module 2, v.2 28.09.2009