Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
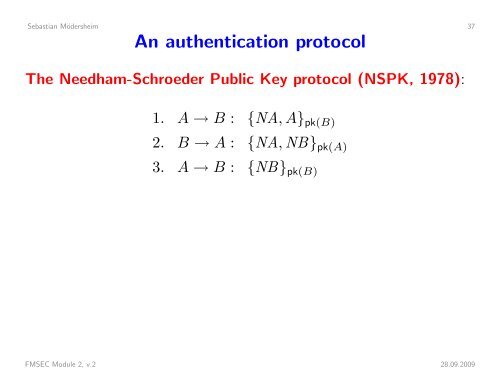
Sebastian Mödersheim 37An authentication protocolThe Needham-Schroeder Public Key protocol (NSPK, 1978):1. A → B : {NA, A} pk(B)2. B → A : {NA, NB} pk(A)3. A → B : {NB} pk(B)FMSEC Module 2, v.2 28.09.2009