Security Protocols I - Information Security
Security Protocols I - Information Security
Security Protocols I - Information Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
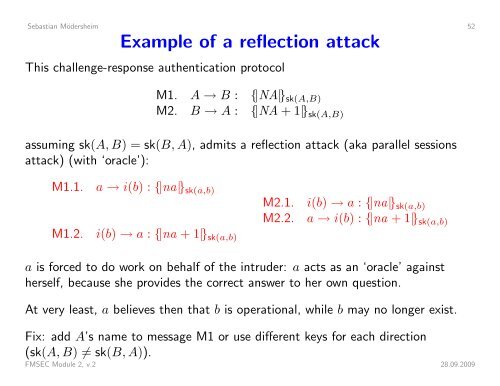
Sebastian Mödersheim 52Example of a reflection attackThis challenge-response authentication protocolM1. A → B : {|NA|} sk(A,B)M2. B → A : {|NA + 1|} sk(A,B)assuming sk(A, B) = sk(B, A), admits a reflection attack (aka parallel sessionsattack) (with ‘oracle’):M1.2.M1.1. a → i(b) : {|na|} sk(a,b)M2.1. i(b) → a : {|na|} sk(a,b)i(b) → a : {|na + 1|} sk(a,b)M2.2.a → i(b) : {|na + 1|} sk(a,b)a is forced to do work on behalf of the intruder: a acts as an ‘oracle’ againstherself, because she provides the correct answer to her own question.At very least, a believes then that b is operational, while b may no longer exist.Fix: add A’s name to message M1 or use different keys for each direction(sk(A, B) ≠ sk(B, A)).FMSEC Module 2, v.2 28.09.2009