ISSUE 91 : Nov/Dec - 1991 - Australian Defence Force Journal
ISSUE 91 : Nov/Dec - 1991 - Australian Defence Force Journal
ISSUE 91 : Nov/Dec - 1991 - Australian Defence Force Journal
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
' " > • '<br />
2S AUSTRALIAN DFFENCF FORCE JOURNAL NO. <strong>91</strong> NOVEMBER DECEMBER 19<strong>91</strong><br />
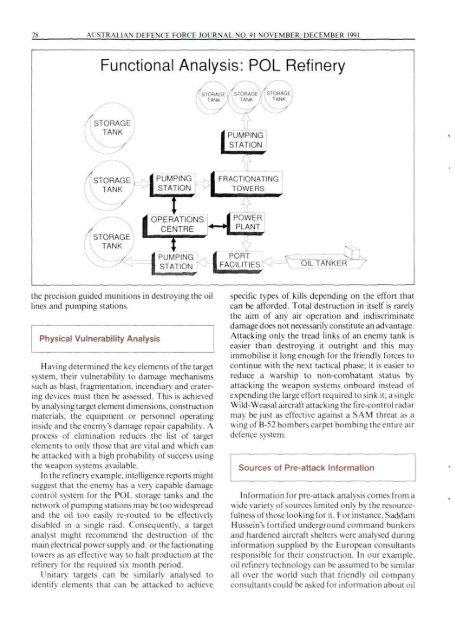
Functional Analysis: POL Refinery<br />
i PUMPING<br />
| STATION<br />
PUMPING<br />
STATION<br />
| FRACTIONATING<br />
L; TOWERS<br />
OPERATIONS<br />
CENTRE<br />
| POWER<br />
*~*L^<br />
PUMPING<br />
STATION '<br />
i PORT<br />
1 FACILITIES' OIL TANKER<br />
the precision guided munitions in destroying the oil<br />
lines and pumping stations.<br />
Physical Vulnerability Analysis<br />
Having determined the key elements of the target<br />
system, their vulnerability to damage mechanisms<br />
such as blast, fragmentation, incendiary and cratering<br />
devices must then be assessed. This is achieved<br />
by analysing target element dimensions, construction<br />
materials, the equipment or personnel operating<br />
inside and the enemy's damage repair capability. A<br />
process of elimination reduces the list of target<br />
elements to only those that are vital and which can<br />
be attacked with a high probability of success using<br />
the weapon systems available.<br />
In the refinery example, intelligence reports might<br />
suggest that the enemy has a very capable damage<br />
control system for the POL storage tanks and the<br />
network of pumping stations may be too widespread<br />
and the oil too easily re-routed to be effectively<br />
disabled in a single raid. Consequently, a target<br />
analyst might recommend the destruction of the<br />
main electrical power supply and, or the factionating<br />
towers as an effective way to halt production at the<br />
refinery for the required six month period.<br />
Unitary targets can be similarly analysed to<br />
identify elements that can be attacked to achieve<br />
specific types of kills depending on the effort that<br />
can be afforded. Total destruction in itself is rarely<br />
the aim of any air operation and indiscriminate<br />
damage does not necessarily constitute an advantage.<br />
Attacking only the tread links of an enemy tank is<br />
easier than destroying it outright and this may<br />
immobilise it long enough for the friendly forces to<br />
continue with the next tactical phase; it is easier to<br />
reduce a warship to non-combatant status by<br />
attacking the weapon systems onboard instead of<br />
expending the large effort required to sink it; a single<br />
Wild-Weasal aircraft attacking the fire-control radar<br />
may be just as effective against a SAM threat as a<br />
wing of B-52 bombers carpet bombing the entire air<br />
defence system.<br />
Sources of Pre-attack Information<br />
Information for pre-attack analysis comes from a<br />
wide variety of sources limited only by the resourcefulness<br />
of those looking for it. For instance, Saddam<br />
Hussein's fortified underground command bunkers<br />
and hardened aircraft shelters were analysed during<br />
information supplied b\ the I'uropean consultants<br />
responsible for their construction. In our example,<br />
oil refinery technology can be assumed to be similar<br />
all over the world such that friendly oil company<br />
consultants could be asked for information about oil