System Architecture Design
System Architecture Design
System Architecture Design
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
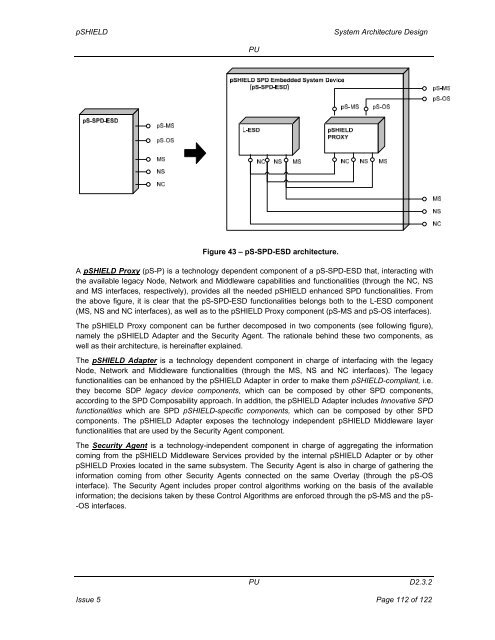
pSHIELD<strong>System</strong> <strong>Architecture</strong> <strong>Design</strong>PUFigure 43 – pS-SPD-ESD architecture.A pSHIELD Proxy (pS-P) is a technology dependent component of a pS-SPD-ESD that, interacting withthe available legacy Node, Network and Middleware capabilities and functionalities (through the NC, NSand MS interfaces, respectively), provides all the needed pSHIELD enhanced SPD functionalities. Fromthe above figure, it is clear that the pS-SPD-ESD functionalities belongs both to the L-ESD component(MS, NS and NC interfaces), as well as to the pSHIELD Proxy component (pS-MS and pS-OS interfaces).The pSHIELD Proxy component can be further decomposed in two components (see following figure),namely the pSHIELD Adapter and the Security Agent. The rationale behind these two components, aswell as their architecture, is hereinafter explained.The pSHIELD Adapter is a technology dependent component in charge of interfacing with the legacyNode, Network and Middleware functionalities (through the MS, NS and NC interfaces). The legacyfunctionalities can be enhanced by the pSHIELD Adapter in order to make them pSHIELD-compliant, i.e.they become SDP legacy device components, which can be composed by other SPD components,according to the SPD Composability approach. In addition, the pSHIELD Adapter includes Innovative SPDfunctionalities which are SPD pSHIELD-specific components, which can be composed by other SPDcomponents. The pSHIELD Adapter exposes the technology independent pSHIELD Middleware layerfunctionalities that are used by the Security Agent component.The Security Agent is a technology-independent component in charge of aggregating the informationcoming from the pSHIELD Middleware Services provided by the internal pSHIELD Adapter or by otherpSHIELD Proxies located in the same subsystem. The Security Agent is also in charge of gathering theinformation coming from other Security Agents connected on the same Overlay (through the pS-OSinterface). The Security Agent includes proper control algorithms working on the basis of the availableinformation; the decisions taken by these Control Algorithms are enforced through the pS-MS and the pS--OS interfaces.PUD2.3.2Issue 5 Page 112 of 122