System Architecture Design
System Architecture Design
System Architecture Design
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
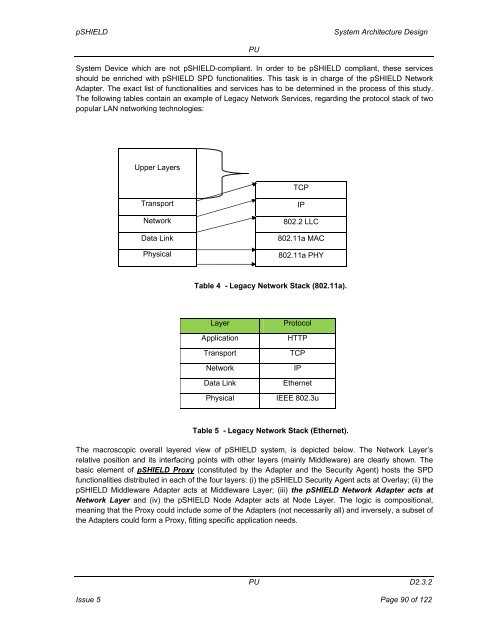
pSHIELD<strong>System</strong> <strong>Architecture</strong> <strong>Design</strong>PU<strong>System</strong> Device which are not pSHIELD-compliant. In order to be pSHIELD compliant, these servicesshould be enriched with pSHIELD SPD functionalities. This task is in charge of the pSHIELD NetworkAdapter. The exact list of functionalities and services has to be determined in the process of this study.The following tables contain an example of Legacy Network Services, regarding the protocol stack of twopopular LAN networking technologies:Upper LayersTCPTransportNetworkData LinkPhysicalIP802.2 LLC802.11a MAC802.11a PHYTable 4 - Legacy Network Stack (802.11a).LayerApplicationTransportNetworkData LinkProtocolHTTPTCPIPEthernetPhysical IEEE 802.3uTable 5 - Legacy Network Stack (Ethernet).The macroscopic overall layered view of pSHIELD system, is depicted below. The Network Layer’srelative position and its interfacing points with other layers (mainly Middleware) are clearly shown. Thebasic element of pSHIELD Proxy (constituted by the Adapter and the Security Agent) hosts the SPDfunctionalities distributed in each of the four layers: (i) the pSHIELD Security Agent acts at Overlay; (ii) thepSHIELD Middleware Adapter acts at Middleware Layer; (iii) the pSHIELD Network Adapter acts atNetwork Layer and (iv) the pSHIELD Node Adapter acts at Node Layer. The logic is compositional,meaning that the Proxy could include some of the Adapters (not necessarily all) and inversely, a subset ofthe Adapters could form a Proxy, fitting specific application needs.PUD2.3.2Issue 5 Page 90 of 122