System Architecture Design
System Architecture Design
System Architecture Design
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
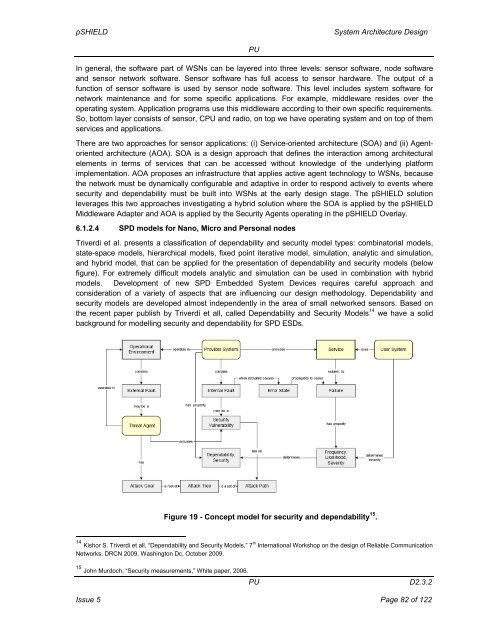
pSHIELD<strong>System</strong> <strong>Architecture</strong> <strong>Design</strong>PUIn general, the software part of WSNs can be layered into three levels: sensor software, node softwareand sensor network software. Sensor software has full access to sensor hardware. The output of afunction of sensor software is used by sensor node software. This level includes system software fornetwork maintenance and for some specific applications. For example, middleware resides over theoperating system. Application programs use this middleware according to their own specific requirements.So, bottom layer consists of sensor, CPU and radio, on top we have operating system and on top of themservices and applications.There are two approaches for sensor applications: (i) Service-oriented architecture (SOA) and (ii) Agentorientedarchitecture (AOA). SOA is a design approach that defines the interaction among architecturalelements in terms of services that can be accessed without knowledge of the underlying platformimplementation. AOA proposes an infrastructure that applies active agent technology to WSNs, becausethe network must be dynamically configurable and adaptive in order to respond actively to events wheresecurity and dependability must be built into WSNs at the early design stage. The pSHIELD solutionleverages this two approaches investigating a hybrid solution where the SOA is applied by the pSHIELDMiddleware Adapter and AOA is applied by the Security Agents operating in the pSHIELD Overlay.6.1.2.4 SPD models for Nano, Micro and Personal nodesTriverdi et al. presents a classification of dependability and security model types: combinatorial models,state-space models, hierarchical models, fixed point iterative model, simulation, analytic and simulation,and hybrid model, that can be applied for the presentation of dependability and security models (belowfigure). For extremely difficult models analytic and simulation can be used in combination with hybridmodels. Development of new SPD Embedded <strong>System</strong> Devices requires careful approach andconsideration of a variety of aspects that are influencing our design methodology. Dependability andsecurity models are developed almost independently in the area of small networked sensors. Based onthe recent paper publish by Triverdi et all, called Dependability and Security Models 14 we have a solidbackground for modelling security and dependability for SPD ESDs.Figure 19 - Concept model for security and dependability 15 .14 Kishor S. Triverdi et all, “Dependability and Security Models,” 7 th International Workshop on the design of Reliable CommunicationNetworks, DRCN 2009, Washington Dc, October 2009.15 John Murdoch, “Security measurements,” White paper, 2006.PUD2.3.2Issue 5 Page 82 of 122