System Architecture Design
System Architecture Design
System Architecture Design
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
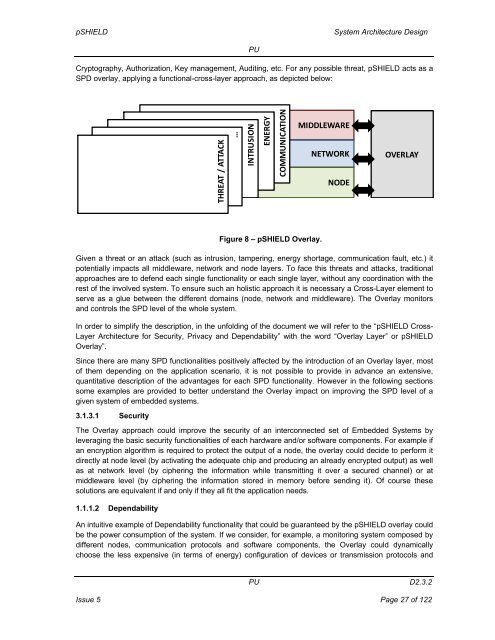
pSHIELD<strong>System</strong> <strong>Architecture</strong> <strong>Design</strong>PUCryptography, Authorization, Key management, Auditing, etc. For any possible threat, pSHIELD acts as aSPD overlay, applying a functional-cross-layer approach, as depicted below:THREAT / ATTACK…INTRUSIONENERGYCOMMUNICATIONMIDDLEWARENETWORKNODEOVERLAYFigure 8 – pSHIELD Overlay.Given a threat or an attack (such as intrusion, tampering, energy shortage, communication fault, etc.) itpotentially impacts all middleware, network and node layers. To face this threats and attacks, traditionalapproaches are to defend each single functionality or each single layer, without any coordination with therest of the involved system. To ensure such an holistic approach it is necessary a Cross-Layer element toserve as a glue between the different domains (node, network and middleware). The Overlay monitorsand controls the SPD level of the whole system.In order to simplify the description, in the unfolding of the document we will refer to the “pSHIELD Cross-Layer <strong>Architecture</strong> for Security, Privacy and Dependability” with the word “Overlay Layer” or pSHIELDOverlay”.Since there are many SPD functionalities positively affected by the introduction of an Overlay layer, mostof them depending on the application scenario, it is not possible to provide in advance an extensive,quantitative description of the advantages for each SPD functionality. However in the following sectionssome examples are provided to better understand the Overlay impact on improving the SPD level of agiven system of embedded systems.3.1.3.1 SecurityThe Overlay approach could improve the security of an interconnected set of Embedded <strong>System</strong>s byleveraging the basic security functionalities of each hardware and/or software components. For example ifan encryption algorithm is required to protect the output of a node, the overlay could decide to perform itdirectly at node level (by activating the adequate chip and producing an already encrypted output) as wellas at network level (by ciphering the information while transmitting it over a secured channel) or atmiddleware level (by ciphering the information stored in memory before sending it). Of course thesesolutions are equivalent if and only if they all fit the application needs.1.1.1.2 DependabilityAn intuitive example of Dependability functionality that could be guaranteed by the pSHIELD overlay couldbe the power consumption of the system. If we consider, for example, a monitoring system composed bydifferent nodes, communication protocols and software components, the Overlay could dynamicallychoose the less expensive (in terms of energy) configuration of devices or transmission protocols andPUD2.3.2Issue 5 Page 27 of 122