NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
GUIDELINES ON SECURING PUBLIC WEB SERVERS<br />
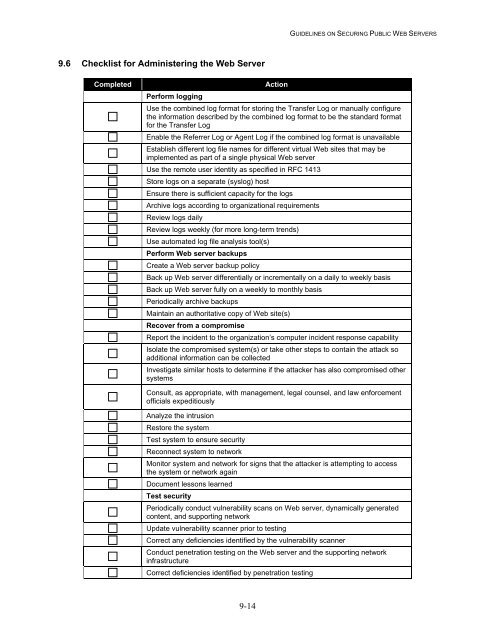
9.6 Checklist for Administering the <strong>Web</strong> Server<br />
Completed<br />
Perform logging<br />
Acti<strong>on</strong><br />
Use the combined log format for storing the Transfer Log or manually c<strong>on</strong>figure<br />
the informati<strong>on</strong> described by the combined log format to be the standard format<br />
for the Transfer Log<br />
Enable the Referrer Log or Agent Log if the combined log format is unavailable<br />
Establish different log file names for different virtual <strong>Web</strong> sites that may be<br />
implemented as part of a single physical <strong>Web</strong> server<br />
Use the remote user identity as specified in RFC 1413<br />
Store logs <strong>on</strong> a separate (syslog) host<br />
Ensure there is sufficient capacity for the logs<br />
Archive logs according to organizati<strong>on</strong>al requirements<br />
Review logs daily<br />
Review logs weekly (for more l<strong>on</strong>g-term trends)<br />
Use automated log file analysis tool(s)<br />
Perform <strong>Web</strong> server backups<br />
Create a <strong>Web</strong> server backup policy<br />
Back up <strong>Web</strong> server differentially or incrementally <strong>on</strong> a daily to weekly basis<br />
Back up <strong>Web</strong> server fully <strong>on</strong> a weekly to m<strong>on</strong>thly basis<br />
Periodically archive backups<br />
Maintain an authoritative copy of <strong>Web</strong> site(s)<br />
Recover from a compromise<br />
Report the incident to the organizati<strong>on</strong>’s computer incident resp<strong>on</strong>se capability<br />
Isolate the compromised system(s) or take other steps to c<strong>on</strong>tain the attack so<br />
additi<strong>on</strong>al informati<strong>on</strong> can be collected<br />
Investigate similar hosts to determine if the attacker has also compromised other<br />
systems<br />
C<strong>on</strong>sult, as appropriate, with management, legal counsel, and law enforcement<br />
officials expeditiously<br />
Analyze the intrusi<strong>on</strong><br />
Restore the system<br />
Test system to ensure security<br />
Rec<strong>on</strong>nect system to network<br />
M<strong>on</strong>itor system and network for signs that the attacker is attempting to access<br />
the system or network again<br />
Document less<strong>on</strong>s learned<br />
Test security<br />
Periodically c<strong>on</strong>duct vulnerability scans <strong>on</strong> <strong>Web</strong> server, dynamically generated<br />
c<strong>on</strong>tent, and supporting network<br />
Update vulnerability scanner prior to testing<br />
Correct any deficiencies identified by the vulnerability scanner<br />
C<strong>on</strong>duct penetrati<strong>on</strong> testing <strong>on</strong> the <strong>Web</strong> server and the supporting network<br />
infrastructure<br />
Correct deficiencies identified by penetrati<strong>on</strong> testing<br />
9-14