NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
NIST 800-44 Version 2 Guidelines on Securing Public Web Servers
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
GUIDELINES ON SECURING PUBLIC WEB SERVERS<br />
offers the most benefits with the least amount of risk for most organizati<strong>on</strong>s. The DMZ allows access to<br />
the resources located within it to both internal and external users. There are a wide variety of DMZ<br />
c<strong>on</strong>figurati<strong>on</strong>s, each with its own strengths and weaknesses.<br />
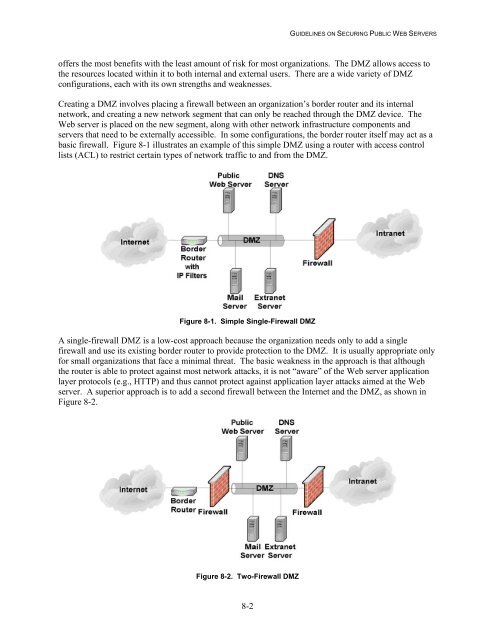
Creating a DMZ involves placing a firewall between an organizati<strong>on</strong>’s border router and its internal<br />
network, and creating a new network segment that can <strong>on</strong>ly be reached through the DMZ device. The<br />
<strong>Web</strong> server is placed <strong>on</strong> the new segment, al<strong>on</strong>g with other network infrastructure comp<strong>on</strong>ents and<br />
servers that need to be externally accessible. In some c<strong>on</strong>figurati<strong>on</strong>s, the border router itself may act as a<br />
basic firewall. Figure 8-1 illustrates an example of this simple DMZ using a router with access c<strong>on</strong>trol<br />
lists (ACL) to restrict certain types of network traffic to and from the DMZ.<br />
Figure 8-1. Simple Single-Firewall DMZ<br />
A single-firewall DMZ is a low-cost approach because the organizati<strong>on</strong> needs <strong>on</strong>ly to add a single<br />
firewall and use its existing border router to provide protecti<strong>on</strong> to the DMZ. It is usually appropriate <strong>on</strong>ly<br />
for small organizati<strong>on</strong>s that face a minimal threat. The basic weakness in the approach is that although<br />
the router is able to protect against most network attacks, it is not “aware” of the <strong>Web</strong> server applicati<strong>on</strong><br />
layer protocols (e.g., HTTP) and thus cannot protect against applicati<strong>on</strong> layer attacks aimed at the <strong>Web</strong><br />
server. A superior approach is to add a sec<strong>on</strong>d firewall between the Internet and the DMZ, as shown in<br />
Figure 8-2.<br />
Figure 8-2. Two-Firewall DMZ<br />
8-2