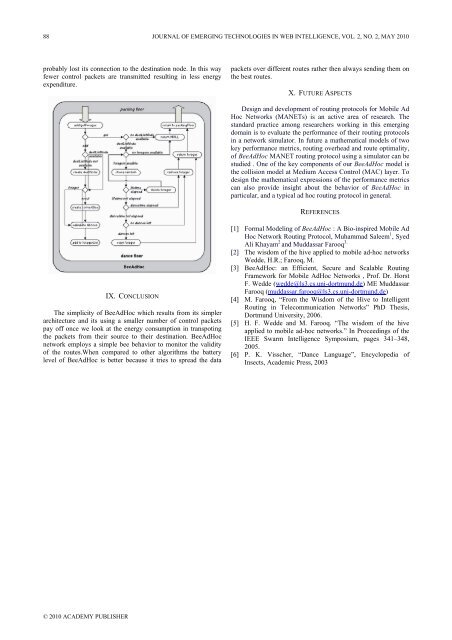
88 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 2, NO. 2, MAY 2010probably lost its connection to the dest<strong>in</strong>ation node. In this wayfewer control packets are transmitted result<strong>in</strong>g <strong>in</strong> less energyexpenditure.packets over different routes rather then always send<strong>in</strong>g them onthe best routes.X. FUTURE ASPECTSDesign and development <strong>of</strong> rout<strong>in</strong>g protocols for Mobile AdHoc Networks (MANETs) is an active area <strong>of</strong> research. Thestandard practice among researchers work<strong>in</strong>g <strong>in</strong> this emerg<strong>in</strong>gdoma<strong>in</strong> is to evaluate the performance <strong>of</strong> their rout<strong>in</strong>g protocols<strong>in</strong> a network simulator. In future a mathematical models <strong>of</strong> twokey performance metrics, rout<strong>in</strong>g overhead and route optimality,<strong>of</strong> BeeAdHoc MANET rout<strong>in</strong>g protocol us<strong>in</strong>g a simulator can bestudied . One <strong>of</strong> the key components <strong>of</strong> our BeeAdHoc model isthe collision model at Medium Access Control (MAC) layer. Todesign the mathematical expressions <strong>of</strong> the performance metricscan also provide <strong>in</strong>sight about the behavior <strong>of</strong> BeeAdHoc <strong>in</strong>particular, and a typical ad hoc rout<strong>in</strong>g protocol <strong>in</strong> general.REFERENCESIX. CONCLUSIONThe simplicity <strong>of</strong> BeeAdHoc which results from its simplerarchitecture and its us<strong>in</strong>g a smaller number <strong>of</strong> control packetspay <strong>of</strong>f once we look at the energy consumption <strong>in</strong> transpot<strong>in</strong>gthe packets from their source to their dest<strong>in</strong>ation. BeeAdHocnetwork employs a simple bee behavior to monitor the validity<strong>of</strong> the routes.When compared to other algorithms the batterylevel <strong>of</strong> BeeAdHoc is better because it tries to spread the data[1] Formal Model<strong>in</strong>g <strong>of</strong> BeeAdHoc : A Bio-<strong>in</strong>spired Mobile AdHoc Network Rout<strong>in</strong>g Protocol, Muhammad Saleem 1 , SyedAli Khayam 2 and Muddassar Farooq 3.[2] The wisdom <strong>of</strong> the hive applied to mobile ad-hoc networksWedde, H.R.; Farooq, M.[3] BeeAdHoc: an Efficient, Secure and Scalable Rout<strong>in</strong>gFramework for Mobile AdHoc Networks , Pr<strong>of</strong>. Dr. HorstF. Wedde (wedde@ls3.cs.uni-dortmund.de) ME MuddassarFarooq (muddassar.farooq@ls3.cs.uni-dortmund.de)[4] M. Farooq, “From the Wisdom <strong>of</strong> the Hive to IntelligentRout<strong>in</strong>g <strong>in</strong> Telecommunication Networks” PhD Thesis,Dortmund University, 2006.[5] H. F. Wedde and M. Farooq. “The wisdom <strong>of</strong> the hiveapplied to mobile ad-hoc networks.” In Proceed<strong>in</strong>gs <strong>of</strong> theIEEE Swarm <strong>Intelligence</strong> Symposium, pages 341–348,2005.[6] P. K. Visscher, “Dance Language”, Encyclopedia <strong>of</strong>Insects, Academic Press, 2003© 2010 ACADEMY PUBLISHER
JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 2, NO. 2, MAY 2010 89Distance and Frequency based Route StabilityEstimation <strong>in</strong> Mobile Adhoc NetworksAjay KoulSMVD University/ School <strong>of</strong> computer Science and Eng<strong>in</strong>eer<strong>in</strong>g, Katra, IndiaEmail:ajay.kaul@smvdu.ac.<strong>in</strong>R. B. Patel and V. K. BhatM.M.University/Department <strong>of</strong> Computer Science and Eng<strong>in</strong>eer<strong>in</strong>g, Ambala, IndiaSMVD University/School <strong>of</strong> Applied Physics and Mathematics, Katra, IndiaEmail :{ patel_r_b, vijaykumarbhat2000}@yahoo.comAbstract-This paper discusses the l<strong>in</strong>k stability estimationfor Mobile Ad hoc Networks (MANETs). In this approachthe total time for which the l<strong>in</strong>k rema<strong>in</strong>s connected with theneighbor<strong>in</strong>g nodes is estimated. This helps to predict thestability <strong>of</strong> the route which is required to forward thepackets to the dest<strong>in</strong>ation. This method does not use theselection <strong>of</strong> the next hop on the basis <strong>of</strong> shortest distance,but is based on the time period for which the next hop l<strong>in</strong>krema<strong>in</strong>s connected. The parameters we use, are the distanceand frequency and signal quality. These provide the way fora node to decide the best next hop neighbor and hence aperfect Quality <strong>of</strong> Service (QoS) is also obta<strong>in</strong>ed.The rest <strong>of</strong> the paper is organized as follows.In Section II we discuss the related works. In Section III,the node distance, position and mobility is estimated.The quality <strong>of</strong> signal along with the algorithms to beexecuted on <strong>in</strong>termediate and dest<strong>in</strong>ation nodes arepresented <strong>in</strong> Section IV. In Section V the practicalscenario <strong>of</strong> estimat<strong>in</strong>g the parameters like distance,frequency, mobility, RSSI, etc. and their performanceresults are obta<strong>in</strong>ed. F<strong>in</strong>ally the article is concluded <strong>in</strong>Sections VI.Index Terms— Route stability, frequency, distance,MANETs, QoS.I. INTRODUCTIONAn ad hoc network is a dynamic multihop wirelessnetwork that is established by a set <strong>of</strong> mobilenodes. Such networks are, therefore, suitable for theenvironments where it is a difficult to create a fixed<strong>in</strong>frastructure. In this network, mobile nodes randomlymove and communicate over radio channels. If twomobile nodes are <strong>in</strong> a radio transmission range, they cancommunicate with each other directly, otherwise, thesource node sends/receives the packets via some<strong>in</strong>termediate nodes. Hence a proper rout<strong>in</strong>g algorithm isrequired to route the packets from source to dest<strong>in</strong>ation.Most rout<strong>in</strong>g algorithms, like <strong>in</strong> [1] estimate the l<strong>in</strong>kstability based on the distance between the twoneighbor<strong>in</strong>g nodes. In [2] the electric field as a parameteris used to f<strong>in</strong>d the stable route to the dest<strong>in</strong>ation. Thealgorithm given <strong>in</strong> [3], f<strong>in</strong>ds the best route to thedest<strong>in</strong>ation based on l<strong>in</strong>k perdurability. These, however,do not lead to the reliable solution <strong>in</strong> Mobile Ad hocNetworks (MANETs), as the environments are dynamicand hence the route estimation depends on the factors likemobility and direction as well. In this paper we havetaken these factors <strong>in</strong>to account and the next hop route isselected not on the basis <strong>of</strong> distance only but on mobilityas well. The quality <strong>of</strong> strength is also taken <strong>in</strong>toconsideration. Our results show that our method can alsobe applied <strong>in</strong> the selection <strong>of</strong> the best neighbor<strong>in</strong>g node.II. RELATED WORKMany rout<strong>in</strong>g protocols <strong>in</strong> the past have been proposed onroute stability. In [4] the technique <strong>of</strong> signal stability isused for adaptive rout<strong>in</strong>g <strong>in</strong> Mobile Ad hoc networks. Inthis approach the on demand longer lived routes arediscovered based on signal strength and location stability.The signal strength <strong>of</strong> the neighbor<strong>in</strong>g nodes are detectedby send<strong>in</strong>g beacons, and based on that, the classification<strong>of</strong> strong and weaker channels are established. This isfurther strengthened by choos<strong>in</strong>g a channel which hasexisted for a longer period <strong>of</strong> time. This signal strengthfeature <strong>in</strong> comb<strong>in</strong>ation with the location stability helps <strong>in</strong>selection <strong>of</strong> the next hop neighbor and hence the overallroute is established. The protocol mentioned even thoughgives good results <strong>in</strong> establish<strong>in</strong>g stable route, however,fails when the node density <strong>in</strong>creases or the node mobility<strong>in</strong>creases. The Global position<strong>in</strong>g system based reliableroute discovery proposed <strong>in</strong> [5] used a different approach.The algorithm discovers routes based on two zones, thestable zone and the caution zone. The zones are decidedbased on the location and the mobility <strong>of</strong> the nodes us<strong>in</strong>gthe Global position<strong>in</strong>g system (GPS). The stable zone andthe caution zone change dynamically depend<strong>in</strong>g on themobile nodes speed and direction <strong>in</strong>formation. Themobile nodes speed, direction and position is estimatedbased on GPS system. This method is the perfect method<strong>of</strong> determ<strong>in</strong><strong>in</strong>g the stability <strong>of</strong> the route as the criticalparameters like direction and mobility is determ<strong>in</strong>ed. Themethod mentioned however, has a serious drawback <strong>of</strong>additional cost <strong>in</strong>volvement and more power requirementfor the GPS based device. In [6] a model to f<strong>in</strong>d the best© 2010 ACADEMY PUBLISHERdoi:10.4304/jetwi.2.2.89-95