Journal of Emerging Technologies in Web Intelligence Contents
Journal of Emerging Technologies in Web Intelligence Contents
Journal of Emerging Technologies in Web Intelligence Contents
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
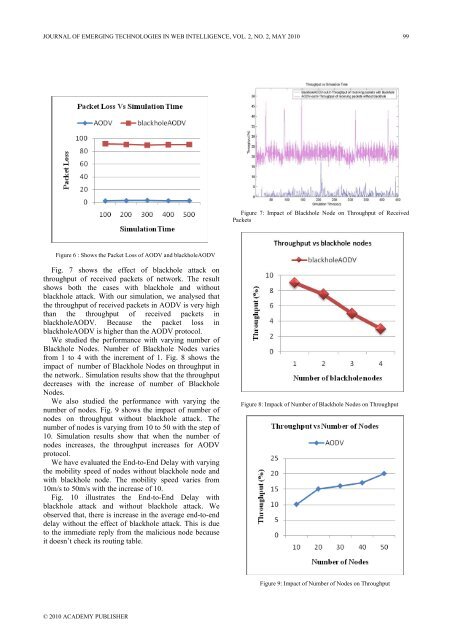
JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 2, NO. 2, MAY 2010 99Figure 7: Impact <strong>of</strong> Blackhole Node on Throughput <strong>of</strong> ReceivedPacketsFigure 6 : Shows the Packet Loss <strong>of</strong> AODV and blackholeAODVFig. 7 shows the effect <strong>of</strong> blackhole attack onthroughput <strong>of</strong> received packets <strong>of</strong> network. The resultshows both the cases with blackhole and withoutblackhole attack. With our simulation, we analysed thatthe throughput <strong>of</strong> received packets <strong>in</strong> AODV is very highthan the throughput <strong>of</strong> received packets <strong>in</strong>blackholeAODV. Because the packet loss <strong>in</strong>blackholeAODV is higher than the AODV protocol.We studied the performance with vary<strong>in</strong>g number <strong>of</strong>Blackhole Nodes. Number <strong>of</strong> Blackhole Nodes variesfrom 1 to 4 with the <strong>in</strong>crement <strong>of</strong> 1. Fig. 8 shows theimpact <strong>of</strong> number <strong>of</strong> Blackhole Nodes on throughput <strong>in</strong>the network.. Simulation results show that the throughputdecreases with the <strong>in</strong>crease <strong>of</strong> number <strong>of</strong> BlackholeNodes.We also studied the performance with vary<strong>in</strong>g thenumber <strong>of</strong> nodes. Fig. 9 shows the impact <strong>of</strong> number <strong>of</strong>nodes on throughput without blackhole attack. Thenumber <strong>of</strong> nodes is vary<strong>in</strong>g from 10 to 50 with the step <strong>of</strong>10. Simulation results show that when the number <strong>of</strong>nodes <strong>in</strong>creases, the throughput <strong>in</strong>creases for AODVprotocol.We have evaluated the End-to-End Delay with vary<strong>in</strong>gthe mobility speed <strong>of</strong> nodes without blackhole node andwith blackhole node. The mobility speed varies from10m/s to 50m/s with the <strong>in</strong>crease <strong>of</strong> 10.Fig. 10 illustrates the End-to-End Delay withblackhole attack and without blackhole attack. Weobserved that, there is <strong>in</strong>crease <strong>in</strong> the average end-to-enddelay without the effect <strong>of</strong> blackhole attack. This is dueto the immediate reply from the malicious node becauseit doesn’t check its rout<strong>in</strong>g table.Figure 8: Impack <strong>of</strong> Number <strong>of</strong> Blackhole Nodes on ThroughputFigure 9: Impact <strong>of</strong> Number <strong>of</strong> Nodes on Throughput© 2010 ACADEMY PUBLISHER