Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
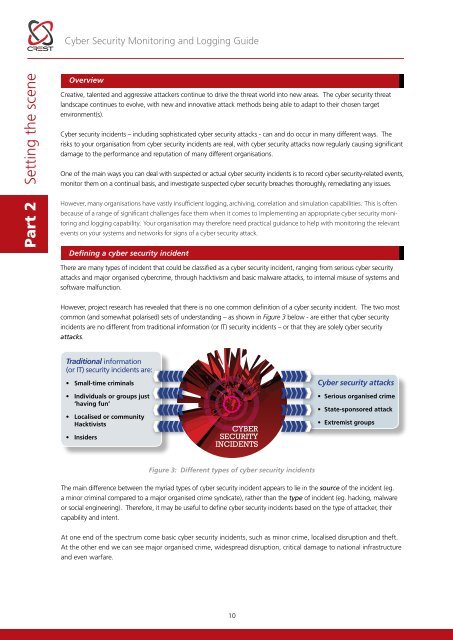
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Part 2 Setting the sceneOverviewCreative, talented and aggressive attackers continue to drive the threat world into new areas. The cyber security threatlandscape continues to evolve, with new and innovative attack methods being able to adapt to their chosen targetenvironment(s).<strong>Cyber</strong> security incidents – including sophisticated cyber security attacks - can and do occur in many different ways. Therisks to your organisation from cyber security incidents are real, with cyber security attacks now regularly causing significantdamage to the performance and reputation of many different organisations.One of the main ways you can deal with suspected or actual cyber security incidents is to record cyber security-related events,monitor them on a continual basis, and investigate suspected cyber security breaches thoroughly, remediating any issues.However, many organisations have vastly insufficient logging, archiving, correlation and simulation capabilities. This is oftenbecause of a range of significant challenges face them when it comes to implementing an appropriate cyber security monitoringand logging capability. Your organisation may therefore need practical guidance to help with monitoring the relevantevents on your systems and networks for signs of a cyber security attack.Defining a cyber security incidentThere are many types of incident that could be classified as a cyber security incident, ranging from serious cyber securityattacks and major organised cybercrime, through hacktivism and basic malware attacks, to internal misuse of systems andsoftware malfunction.However, project research has revealed that there is no one common definition of a cyber security incident. The two mostcommon (and somewhat polarised) sets of understanding – as shown in Figure 3 below - are either that cyber securityincidents are no different from traditional information (or IT) security incidents – or that they are solely cyber securityattacks.Traditional information(or IT) security incidents are:• Small-time criminals• Individuals or groups just‘having fun’• Localised or communityHacktivists• InsidersCYBERSECURITYINCIDENTS<strong>Cyber</strong> security attacks• Serious organised crime• State-sponsored attack• Extremist groupsFigure 3: Different types of cyber security incidentsThe main difference between the myriad types of cyber security incident appears to lie in the source of the incident (eg.a minor criminal compared to a major organised crime syndicate), rather than the type of incident (eg. hacking, malwareor social engineering). Therefore, it may be useful to define cyber security incidents based on the type of attacker, theircapability and intent.At one end of the spectrum come basic cyber security incidents, such as minor crime, localised disruption and theft.At the other end we can see major organised crime, widespread disruption, critical damage to national infrastructureand even warfare.10