Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
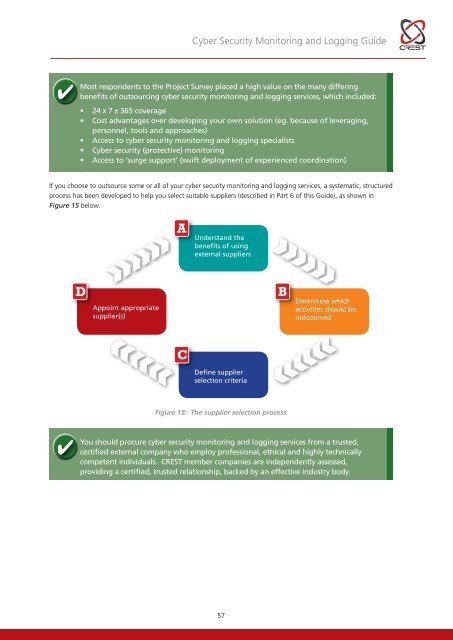
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Most respondents to the Project Survey placed a high value on the many differingbenefits of outsourcing cyber security monitoring and logging services, which included:• 24 x 7 x 365 coverage• Cost advantages over developing your own solution (eg. because of leveraging,personnel, tools and approaches)• Access to cyber security monitoring and logging specialists• <strong>Cyber</strong> security (protective) monitoring• Access to ‘surge support’ (swift deployment of experienced coordination)If you choose to outsource some or all of your cyber security monitoring and logging services, a systematic, structuredprocess has been developed to help you select suitable suppliers (described in Part 6 of this <strong>Guide</strong>), as shown inFigure 15 below.AUnderstand thebenefits of usingexternal suppliersDAppoint appropriatesupplier(s)BDetermine whichactivities should beoutsourcedCDefine supplierselection criteriaFigure 15: The supplier selection processYou should procure cyber security monitoring and logging services from a trusted,certified external company who employ professional, ethical and highly technicallycompetent individuals. CREST member companies are independently assessed,providing a certified, trusted relationship, backed by an effective industry body.57