Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
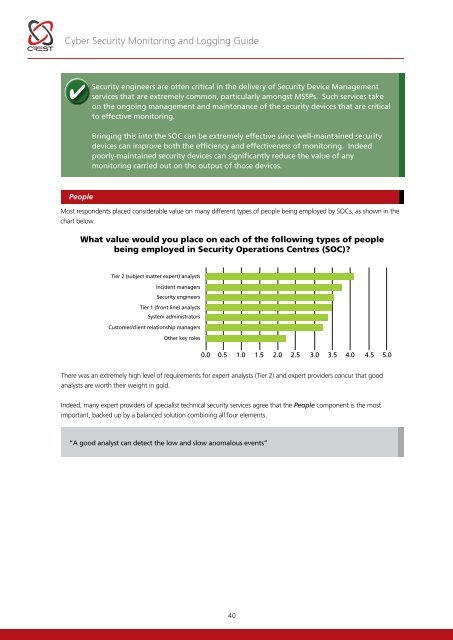
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong><strong>Security</strong> engineers are often critical in the delivery of <strong>Security</strong> Device Managementservices that are extremely common, particularly amongst MSSPs. Such services takeon the ongoing management and maintenance of the security devices that are criticalto effective monitoring.Bringing this into the SOC can be extremely effective since well-maintained securitydevices can improve both the efficiency and effectiveness of monitoring. Indeedpoorly-maintained security devices can significantly reduce the value of anymonitoring carried out on the output of those devices.PeopleMost respondents placed considerable value on many different types of people being employed by SOCs, as shown in thechart below.What value would you place on each of the following types of peoplebeing employed in <strong>Security</strong> Operations Centres (SOC)?Tier 2 (subject matter expert) analystsIncident managers<strong>Security</strong> engineersTier 1 (front line) analystsSystem administratorsCustomer/client relationship managersOther key roles0.0 0.5 1.0 1.5 2.02.5 3.0 3.5 4.0 4.5 5.0There was an extremely high level of requirements for expert analysts (Tier 2) and expert providers concur that goodanalysts are worth their weight in gold.Indeed, many expert providers of specialist technical security services agree that the People component is the mostimportant, backed up by a balanced solution combining all four elements.“A good analyst can detect the low and slow anomalous events”40