Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
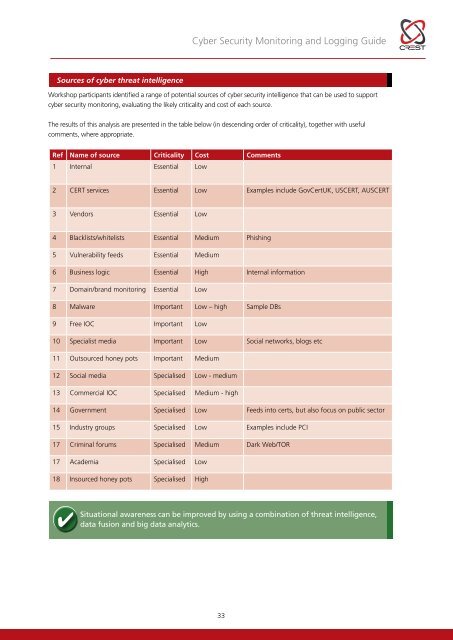
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Sources of cyber threat intelligenceWorkshop participants identified a range of potential sources of cyber security intelligence that can be used to supportcyber security monitoring, evaluating the likely criticality and cost of each source.The results of this analysis are presented in the table below (in descending order of criticality), together with usefulcomments, where appropriate.Ref Name of source Criticality Cost Comments1 Internal Essential Low2 CERT services Essential Low Examples include GovCertUK, USCERT, AUSCERT3 Vendors Essential Low4 Blacklists/whitelists Essential Medium Phishing5 Vulnerability feeds Essential Medium6 Business logic Essential High Internal information7 Domain/brand monitoring Essential Low8 Malware Important Low – high Sample DBs9 Free IOC Important Low10 Specialist media Important Low Social networks, blogs etc11 Outsourced honey pots Important Medium12 Social media Specialised Low - medium13 Commercial IOC Specialised Medium - high14 Government Specialised Low Feeds into certs, but also focus on public sector15 Industry groups Specialised Low Examples include PCI17 Criminal forums Specialised Medium Dark Web/TOR17 Academia Specialised Low18 Insourced honey pots Specialised HighSituational awareness can be improved by using a combination of threat intelligence,data fusion and big data analytics.33