Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
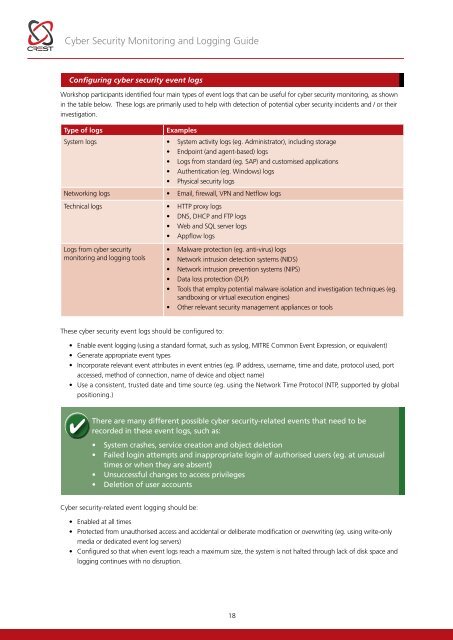
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Configuring cyber security event logsWorkshop participants identified four main types of event logs that can be useful for cyber security monitoring, as shownin the table below. These logs are primarily used to help with detection of potential cyber security incidents and / or theirinvestigation.Type of logsExamplesSystem logs • System activity logs (eg. Administrator), including storage• Endpoint (and agent-based) logs• Logs from standard (eg. SAP) and customised applications• Authentication (eg. Windows) logs• Physical security logsNetworking logs • Email, firewall, VPN and Netflow logsTechnical logs • HTTP proxy logs• DNS, DHCP and FTP logs• Web and SQL server logs• Appflow logsLogs from cyber securitymonitoring and logging tools• Malware protection (eg. anti-virus) logs• Network intrusion detection systems (NIDS)• Network intrusion prevention systems (NIPS)• Data loss protection (DLP)• Tools that employ potential malware isolation and investigation techniques (eg.sandboxing or virtual execution engines)• Other relevant security management appliances or toolsThese cyber security event logs should be configured to:• Enable event logging (using a standard format, such as syslog, MITRE Common Event Expression, or equivalent)• Generate appropriate event types• Incorporate relevant event attributes in event entries (eg. IP address, username, time and date, protocol used, portaccessed, method of connection, name of device and object name)• Use a consistent, trusted date and time source (eg. using the Network Time Protocol (NTP, supported by globalpositioning.)There are many different possible cyber security-related events that need to berecorded in these event logs, such as:• System crashes, service creation and object deletion• Failed login attempts and inappropriate login of authorised users (eg. at unusualtimes or when they are absent)• Unsuccessful changes to access privileges• Deletion of user accounts<strong>Cyber</strong> security-related event logging should be:• Enabled at all times• Protected from unauthorised access and accidental or deliberate modification or overwriting (eg. using write-onlymedia or dedicated event log servers)• Configured so that when event logs reach a maximum size, the system is not halted through lack of disk space andlogging continues with no disruption.18