Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
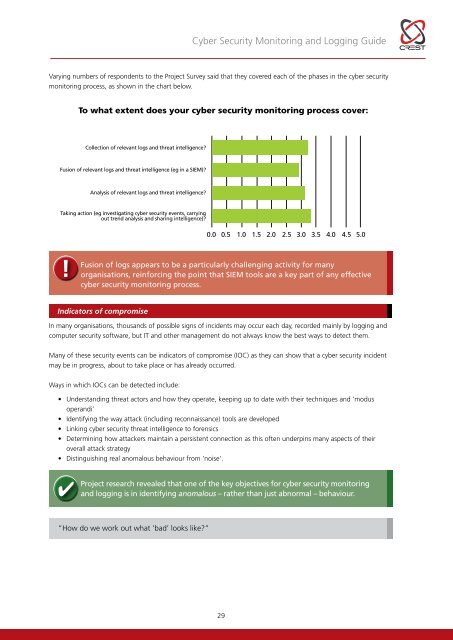
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Varying numbers of respondents to the Project Survey said that they covered each of the phases in the cyber securitymonitoring process, as shown in the chart below.To what extent does your cyber security monitoring process cover:Collection of relevant logs and threat intelligence?Fusion of relevant logs and threat intelligence (eg in a SIEM)?Analysis of relevant logs and threat intelligence?Taking action (eg investigating cyber security events, carryingout trend analysis and sharing intelligence)?0.0 0.5 1.0 1.5 2.02.5 3.0 3.5 4.0 4.5 5.0!Fusion of logs appears to be a particularly challenging activity for manyorganisations, reinforcing the point that SIEM tools are a key part of any effectivecyber security monitoring process.Indicators of compromiseIn many organisations, thousands of possible signs of incidents may occur each day, recorded mainly by logging andcomputer security software, but IT and other management do not always know the best ways to detect them.Many of these security events can be indicators of compromise (IOC) as they can show that a cyber security incidentmay be in progress, about to take place or has already occurred.Ways in which IOCs can be detected include:• Understanding threat actors and how they operate, keeping up to date with their techniques and ‘modusoperandi’• Identifying the way attack (including reconnaissance) tools are developed• Linking cyber security threat intelligence to forensics• Determining how attackers maintain a persistent connection as this often underpins many aspects of theiroverall attack strategy• Distinguishing real anomalous behaviour from ‘noise’.Project research revealed that one of the key objectives for cyber security monitoringand logging is in identifying anomalous – rather than just abnormal – behaviour.“How do we work out what ‘bad’ looks like?”29