Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
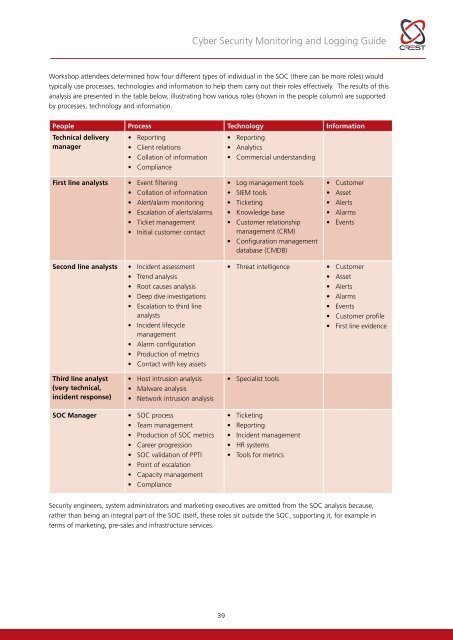
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Workshop attendees determined how four different types of individual in the SOC (there can be more roles) wouldtypically use processes, technologies and information to help them carry out their roles effectively. The results of thisanalysis are presented in the table below, illustrating how various roles (shown in the people column) are supportedby processes, technology and information.People Process Technology InformationTechnical deliverymanager• Reporting• Client relations• Collation of information• Compliance• Reporting• Analytics• Commercial understandingFirst line analysts• Event filtering• Collation of information• Alert/alarm monitoring• Escalation of alerts/alarms• Ticket management• Initial customer contact• Log management tools• SIEM tools• Ticketing• Knowledge base• Customer relationshipmanagement (CRM)• Configuration managementdatabase (CMDB)• Customer• Asset• Alerts• Alarms• EventsSecond line analysts• Incident assessment• Trend analysis• Root causes analysis• Deep dive investigations• Escalation to third lineanalysts• Incident lifecyclemanagement• Alarm configuration• Production of metrics• Contact with key assets• Threat intelligence• Customer• Asset• Alerts• Alarms• Events• Customer profile• First line evidenceThird line analyst(very technical,incident response)• Host intrusion analysis• Malware analysis• Network intrusion analysis• Specialist toolsSOC Manager• SOC process• Team management• Production of SOC metrics• Career progression• SOC validation of PPTI• Point of escalation• Capacity management• Compliance• Ticketing• Reporting• Incident management• HR systems• Tools for metrics<strong>Security</strong> engineers, system administrators and marketing executives are omitted from the SOC analysis because,rather than being an integral part of the SOC itself, these roles sit outside the SOC, supporting it, for example interms of marketing, pre-sales and infrastructure services.39