Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
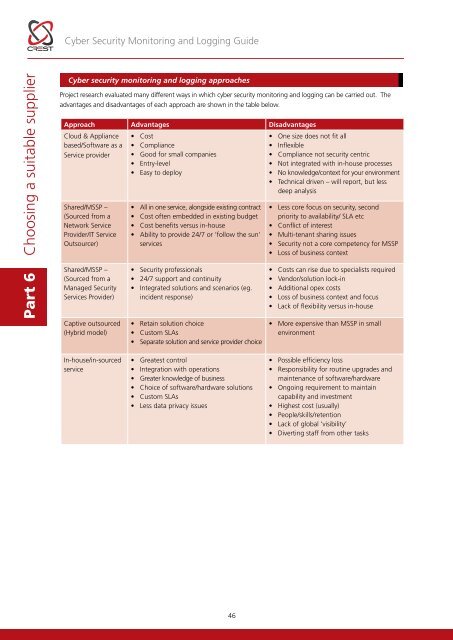
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Part 6 Choosing a suitable supplier<strong>Cyber</strong> security monitoring and logging approachesProject research evaluated many different ways in which cyber security monitoring and logging can be carried out. Theadvantages and disadvantages of each approach are shown in the table below.Approach Advantages DisadvantagesCloud & Appliancebased/Software as aService providerShared/MSSP –(Sourced from aNetwork ServiceProvider/IT ServiceOutsourcer)Shared/MSSP –(Sourced from aManaged <strong>Security</strong>Services Provider)Captive outsourced(Hybrid model)• Cost• Compliance• Good for small companies• Entry-level• Easy to deploy• All in one service, alongside existing contract• Cost often embedded in existing budget• Cost benefits versus in-house• Ability to provide 24/7 or ‘follow the sun’services• <strong>Security</strong> professionals• 24/7 support and continuity• Integrated solutions and scenarios (eg.incident response)• Retain solution choice• Custom SLAs• Separate solution and service provider choice• One size does not fit all• Inflexible• Compliance not security centric• Not integrated with in-house processes• No knowledge/context for your environment• Technical driven – will report, but lessdeep analysis• Less core focus on security, secondpriority to availability/ SLA etc• Conflict of interest• Multi-tenant sharing issues• <strong>Security</strong> not a core competency for MSSP• Loss of business context• Costs can rise due to specialists required• Vendor/solution lock-in• Additional opex costs• Loss of business context and focus• Lack of flexibility versus in-house• More expensive than MSSP in smallenvironmentIn-house/in-sourcedservice• Greatest control• Integration with operations• Greater knowledge of business• Choice of software/hardware solutions• Custom SLAs• Less data privacy issues• Possible efficiency loss• Responsibility for routine upgrades andmaintenance of software/hardware• Ongoing requirement to maintaincapability and investment• Highest cost (usually)• People/skills/retention• Lack of global ‘visibility’• Diverting staff from other tasks46