<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Higher apprenticeship work is currently being carried out (supported by the UKGovernment) to develop learning and development pathways that will lead to betterskilled and suitably qualified people working in the NOCs and SOCs.ProcessProject research identified that many organisations do not have adequate policies, processes or methodologies (if they haveany at all) to help them monitor cyber security-related events effectively. They struggle to know what to do, how to do it,who to contact – and can even compromise investigations by their actions.SOCs are typically supported by different types of processes for different purposes, such as:• Operational (eg. call-out, case management, event management, monitoring, staff management, triage)• Analytical (eg. event analysis, incident response, reporting, research, threat intelligence)• Business and technological (eg. access management, architecture, compliance, BCP, process improvement,use cases).Most respondents placed very high value on many different types of processes being employed by SOCs, the top six being:• Incident response (4.2 out of 5)• Event correlation and analysis (4.1 out of 5)• Signatures, rules and analytic development (including incident investigation, malware analysis, maintenance ofcommercial blacklist and maintenance of intelligence database)• Situational awareness• Threat briefing (including passing on of expertise, feedback on threat intelligence provided, two-way informationtransfer and sharing of investigative resources)• Quality assurance (including addition of signatures, incident review, incident trend monitoring and correlation of newmalware families and analytics).Much of these can be integrated into an effective event analysis process, such as the one outlined on the following page.Expert suppliers of cyber security monitoring services can help you develop anappropriate process – or implement their own tailored version.You should appoint a suitable supplier(s) in advance, who is ready to help at shortnotice, as required (for example by keeping third parties on a retainer for times ofneed). Should you suffer a cyber security incident, you will then be able to undertakefully-fledged breach investigation and eradication quickly and effectively.42
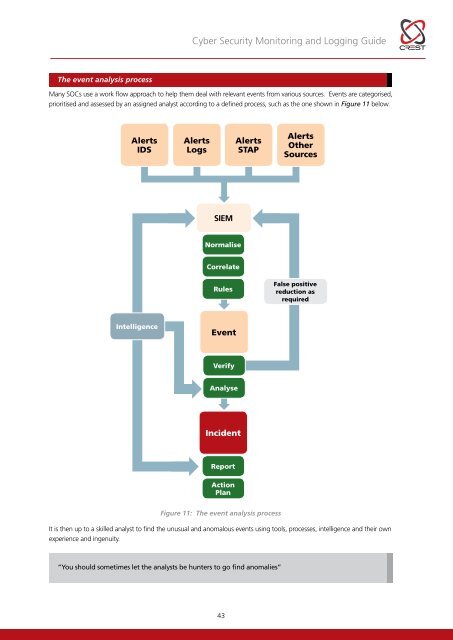
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>The event analysis processMany SOCs use a work flow approach to help them deal with relevant events from various sources. Events are categorised,prioritised and assessed by an assigned analyst according to a defined process, such as the one shown in Figure 11 below.AlertsIDSAlertsLogsAlertsSTAPAlertsOtherSourcesSIEMNormaliseCorrelateRulesFalse positivereduction asrequiredIntelligenceEventVerifyAnalyseIncidentReportActionPlanFigure 11: The event analysis processIt is then up to a skilled analyst to find the unusual and anomalous events using tools, processes, intelligence and their ownexperience and ingenuity.“You should sometimes let the analysts be hunters to go find anomalies”43