Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
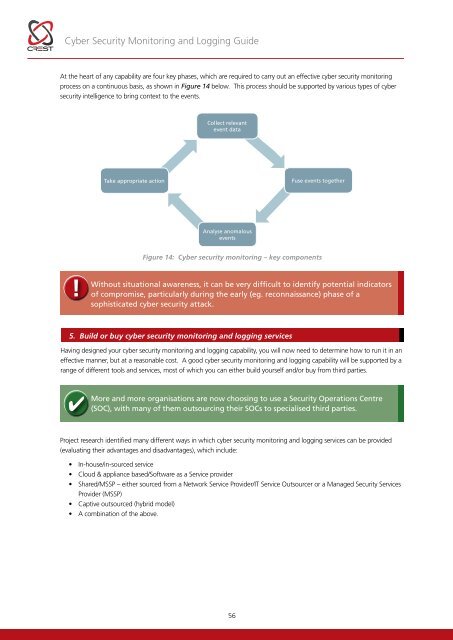
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>At the heart of any capability are four key phases, which are required to carry out an effective cyber security monitoringprocess on a continuous basis, as shown in Figure 14 below. This process should be supported by various types of cybersecurity intelligence to bring context to the events.Collect relevantevent dataTake appropriate actionFuse events togetherAnalyse anomalouseventsFigure 14: <strong>Cyber</strong> security monitoring – key components!Without situational awareness, it can be very difficult to identify potential indicatorsof compromise, particularly during the early (eg. reconnaissance) phase of asophisticated cyber security attack.5. Build or buy cyber security monitoring and logging servicesHaving designed your cyber security monitoring and logging capability, you will now need to determine how to run it in aneffective manner, but at a reasonable cost. A good cyber security monitoring and logging capability will be supported by arange of different tools and services, most of which you can either build yourself and/or buy from third parties.More and more organisations are now choosing to use a <strong>Security</strong> Operations Centre(SOC), with many of them outsourcing their SOCs to specialised third parties.Project research identified many different ways in which cyber security monitoring and logging services can be provided(evaluating their advantages and disadvantages), which include:• In-house/in-sourced service• Cloud & appliance based/Software as a Service provider• Shared/MSSP – either sourced from a Network Service Provider/IT Service Outsourcer or a Managed <strong>Security</strong> ServicesProvider (MSSP)• Captive outsourced (hybrid model)• A combination of the above.56