Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
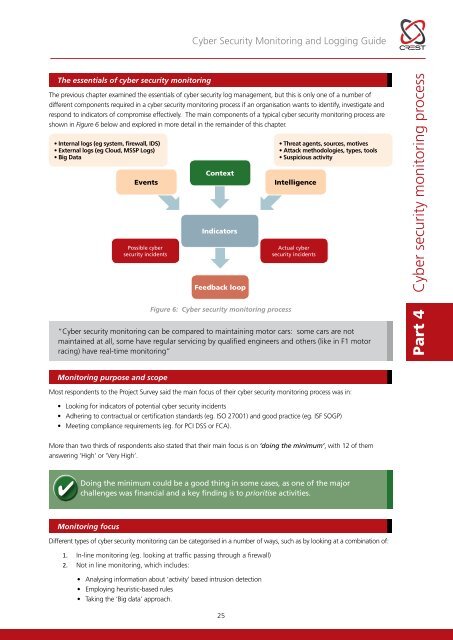
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>The essentials of cyber security monitoringThe previous chapter examined the essentials of cyber security log management, but this is only one of a number ofdifferent components required in a cyber security monitoring process if an organisation wants to identify, investigate andrespond to indicators of compromise effectively. The main components of a typical cyber security monitoring process areshown in Figure 6 below and explored in more detail in the remainder of this chapter.• Internal logs (eg system, firewall, IDS)• External logs (eg Cloud, MSSP Logs)• Big DataEventsPossible cybersecurity incidentsContextIndicatorsFeedback loopFigure 6: <strong>Cyber</strong> security monitoring process• Threat agents, sources, motives• Attack methodologies, types, tools• Suspicious activityIntelligenceActual cybersecurity incidents“<strong>Cyber</strong> security monitoring can be compared to maintaining motor cars: some cars are notmaintained at all, some have regular servicing by qualified engineers and others (like in F1 motorracing) have real-time monitoring”Part 4 <strong>Cyber</strong> security monitoring process<strong>Monitoring</strong> purpose and scopeMost respondents to the Project Survey said the main focus of their cyber security monitoring process was in:• Looking for indicators of potential cyber security incidents• Adhering to contractual or certification standards (eg. ISO 27001) and good practice (eg. ISF SOGP)• Meeting compliance requirements (eg. for PCI DSS or FCA).More than two thirds of respondents also stated that their main focus is on ‘doing the minimum’, with 12 of themanswering ‘High’ or ‘Very High’.Doing the minimum could be a good thing in some cases, as one of the majorchallenges was financial and a key finding is to prioritise activities.<strong>Monitoring</strong> focusDifferent types of cyber security monitoring can be categorised in a number of ways, such as by looking at a combination of:1. In-line monitoring (eg. looking at traffic passing through a firewall)2. Not in line monitoring, which includes:• Analysing information about ‘activity’ based intrusion detection• Employing heuristic-based rules• Taking the ‘Big data’ approach.25