Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
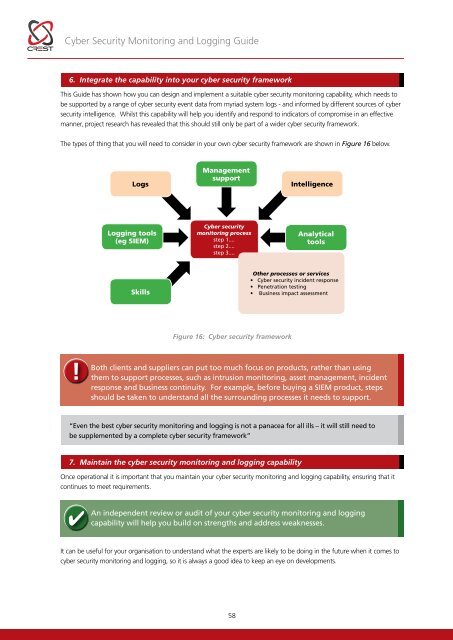
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>6. Integrate the capability into your cyber security frameworkThis <strong>Guide</strong> has shown how you can design and implement a suitable cyber security monitoring capability, which needs tobe supported by a range of cyber security event data from myriad system logs - and informed by different sources of cybersecurity intelligence. Whilst this capability will help you identify and respond to indicators of compromise in an effectivemanner, project research has revealed that this should still only be part of a wider cyber security framework.The types of thing that you will need to consider in your own cyber security framework are shown in Figure 16 below.LogsManagementsupportIntelligenceLogging tools(eg SIEM)<strong>Cyber</strong> securitymonitoring processstep 1....step 2....step 3....AnalyticaltoolsSkillsOther processes or services• <strong>Cyber</strong> security incident response• Penetration testing• Business impact assessmentFigure 16: <strong>Cyber</strong> security framework!Both clients and suppliers can put too much focus on products, rather than usingthem to support processes, such as intrusion monitoring, asset management, incidentresponse and business continuity. For example, before buying a SIEM product, stepsshould be taken to understand all the surrounding processes it needs to support.“Even the best cyber security monitoring and logging is not a panacea for all ills – it will still need tobe supplemented by a complete cyber security framework”7. Maintain the cyber security monitoring and logging capabilityOnce operational it is important that you maintain your cyber security monitoring and logging capability, ensuring that itcontinues to meet requirements.An independent review or audit of your cyber security monitoring and loggingcapability will help you build on strengths and address weaknesses.It can be useful for your organisation to understand what the experts are likely to be doing in the future when it comes tocyber security monitoring and logging, so it is always a good idea to keep an eye on developments.58