Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
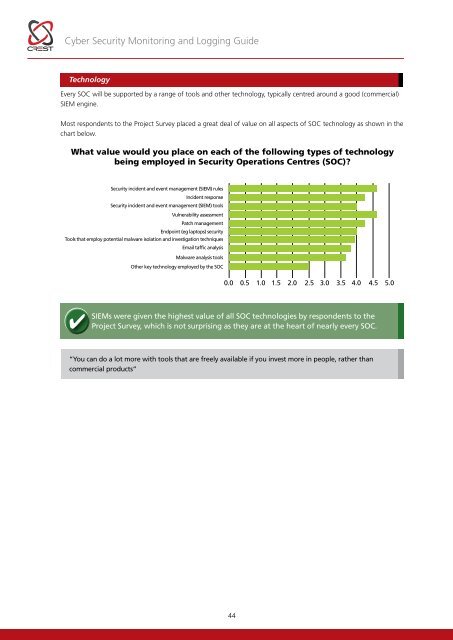
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>TechnologyEvery SOC will be supported by a range of tools and other technology, typically centred around a good (commercial)SIEM engine.Most respondents to the Project Survey placed a great deal of value on all aspects of SOC technology as shown in thechart below.What value would you place on each of the following types of technologybeing employed in <strong>Security</strong> Operations Centres (SOC)?<strong>Security</strong> incident and event management (SIEM) rulesIncident response<strong>Security</strong> incident and event management (SIEM) toolsVulnerability assessmentPatch managementEndpoint (eg laptops) securityTools that employ potential malware isolation and investigation techniquesEmail taffic analysisMalware analysis toolsOther key technology employed by the SOC0.0 0.5 1.0 1.5 2.02.5 3.0 3.5 4.0 4.5 5.0SIEMs were given the highest value of all SOC technologies by respondents to theProject Survey, which is not surprising as they are at the heart of nearly every SOC.“You can do a lot more with tools that are freely available if you invest more in people, rather thancommercial products”44