Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
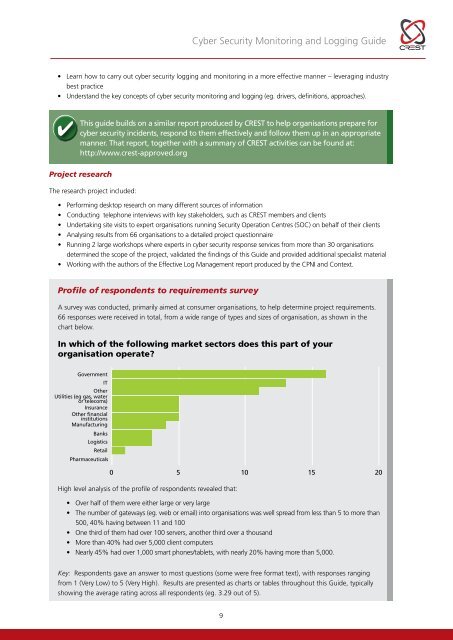
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>• Learn how to carry out cyber security logging and monitoring in a more effective manner – leveraging industrybest practice• Understand the key concepts of cyber security monitoring and logging (eg. drivers, definitions, approaches).This guide builds on a similar report produced by CREST to help organisations prepare forcyber security incidents, respond to them effectively and follow them up in an appropriatemanner. That report, together with a summary of CREST activities can be found at:http://www.crest-approved.orgProject researchThe research project included:• Performing desktop research on many different sources of information• Conducting telephone interviews with key stakeholders, such as CREST members and clients• Undertaking site visits to expert organisations running <strong>Security</strong> Operation Centres (SOC) on behalf of their clients• Analysing results from 66 organisations to a detailed project questionnaire• Running 2 large workshops where experts in cyber security response services from more than 30 organisationsdetermined the scope of the project, validated the findings of this <strong>Guide</strong> and provided additional specialist material• Working with the authors of the Effective Log Management report produced by the CPNI and Context.Profile of respondents to requirements surveyA survey was conducted, primarily aimed at consumer organisations, to help determine project requirements.66 responses were received in total, from a wide range of types and sizes of organisation, as shown in thechart below.In which of the following market sectors does this part of yourorganisation operate?GovernmentITOtherUtilities (eg gas, wateror telecoms)InsuranceOther financialinstitutionsManufacturingBanksLogisticsRetailPharmaceuticals0 5 10 15 20High level analysis of the profile of respondents revealed that:• Over half of them were either large or very large• The number of gateways (eg. web or email) into organisations was well spread from less than 5 to more than500, 40% having between 11 and 100• One third of them had over 100 servers, another third over a thousand• More than 40% had over 5,000 client computers• Nearly 45% had over 1,000 smart phones/tablets, with nearly 20% having more than 5,000.Key: Respondents gave an answer to most questions (some were free format text), with responses rangingfrom 1 (Very Low) to 5 (Very High). Results are presented as charts or tables throughout this <strong>Guide</strong>, typicallyshowing the average rating across all respondents (eg. 3.29 out of 5).9