Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
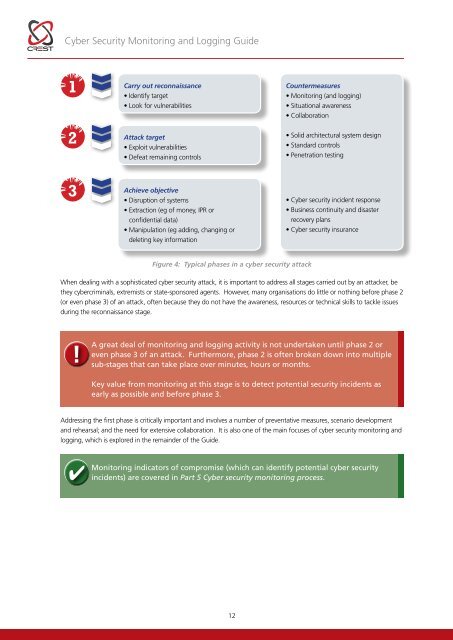
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>12Carry out reconnaissance• Identify target• Look for vulnerabilitiesAttack target• Exploit vulnerabilities• Defeat remaining controlsCountermeasures• <strong>Monitoring</strong> (and logging)• Situational awareness• Collaboration• Solid architectural system design• Standard controls• Penetration testing3Achieve objective• Disruption of systems• Extraction (eg of money, IPR orconfidential data)• Manipulation (eg adding, changing ordeleting key information• <strong>Cyber</strong> security incident response• Business continuity and disasterrecovery plans• <strong>Cyber</strong> security insuranceFigure 4: Typical phases in a cyber security attackWhen dealing with a sophisticated cyber security attack, it is important to address all stages carried out by an attacker, bethey cybercriminals, extremists or state-sponsored agents. However, many organisations do little or nothing before phase 2(or even phase 3) of an attack, often because they do not have the awareness, resources or technical skills to tackle issuesduring the reconnaissance stage.!A great deal of monitoring and logging activity is not undertaken until phase 2 oreven phase 3 of an attack. Furthermore, phase 2 is often broken down into multiplesub-stages that can take place over minutes, hours or months.Key value from monitoring at this stage is to detect potential security incidents asearly as possible and before phase 3.Addressing the first phase is critically important and involves a number of preventative measures, scenario developmentand rehearsal; and the need for extensive collaboration. It is also one of the main focuses of cyber security monitoring andlogging, which is explored in the remainder of the <strong>Guide</strong>.<strong>Monitoring</strong> indicators of compromise (which can identify potential cyber securityincidents) are covered in Part 5 <strong>Cyber</strong> security monitoring process.12