Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
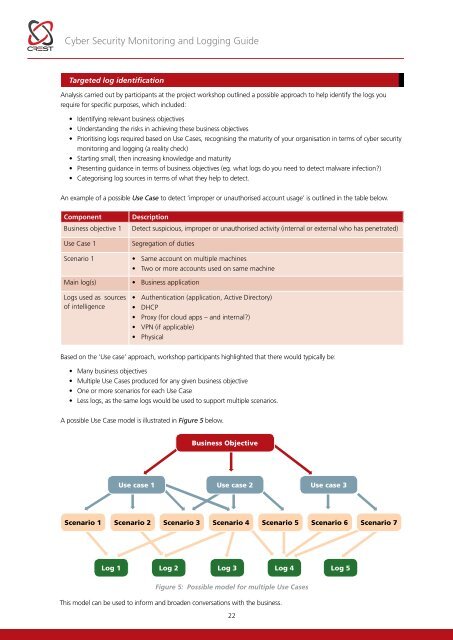
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Targeted log identificationAnalysis carried out by participants at the project workshop outlined a possible approach to help identify the logs yourequire for specific purposes, which included:• Identifying relevant business objectives• Understanding the risks in achieving these business objectives• Prioritising logs required based on Use Cases, recognising the maturity of your organisation in terms of cyber securitymonitoring and logging (a reality check)• Starting small, then increasing knowledge and maturity• Presenting guidance in terms of business objectives (eg. what logs do you need to detect malware infection?)• Categorising log sources in terms of what they help to detect.An example of a possible Use Case to detect ‘improper or unauthorised account usage’ is outlined in the table below.ComponentBusiness objective 1Use Case 1Scenario 1Main log(s)Logs used as sourcesof intelligenceDescriptionDetect suspicious, improper or unauthorised activity (internal or external who has penetrated)Segregation of duties• Same account on multiple machines• Two or more accounts used on same machine• Business application• Authentication (application, Active Directory)• DHCP• Proxy (for cloud apps – and internal?)• VPN (if applicable)• PhysicalBased on the ‘Use case’ approach, workshop participants highlighted that there would typically be:• Many business objectives• Multiple Use Cases produced for any given business objective• One or more scenarios for each Use Case• Less logs, as the same logs would be used to support multiple scenarios.A possible Use Case model is illustrated in Figure 5 below.Business ObjectiveUse case 1 Use case 2 Use case 3Scenario 1Scenario 2 Scenario 3 Scenario 4 Scenario 5 Scenario 6 Scenario 7Log 1Log 2 Log 3 Log 4 Log 5Figure 5: Possible model for multiple Use CasesThis model can be used to inform and broaden conversations with the business.22