Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
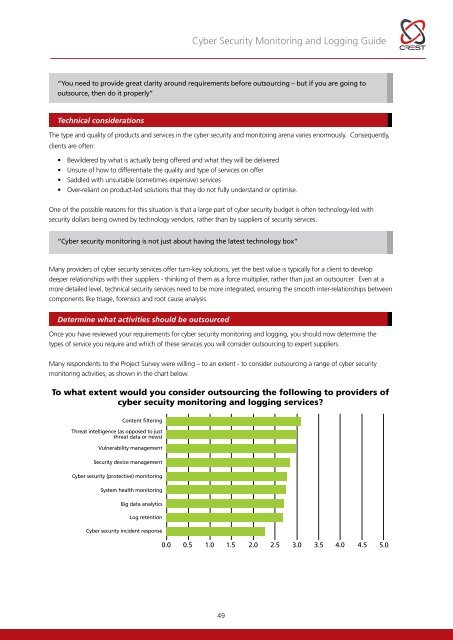
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>“You need to provide great clarity around requirements before outsourcing – but if you are going tooutsource, then do it properly”Technical considerationsThe type and quality of products and services in the cyber security and monitoring arena varies enormously. Consequently,clients are often:• Bewildered by what is actually being offered and what they will be delivered• Unsure of how to differentiate the quality and type of services on offer• Saddled with unsuitable (sometimes expensive) services• Over-reliant on product-led solutions that they do not fully understand or optimise.One of the possible reasons for this situation is that a large part of cyber security budget is often technology-led withsecurity dollars being owned by technology vendors, rather than by suppliers of security services.“<strong>Cyber</strong> security monitoring is not just about having the latest technology box”Many providers of cyber security services offer turn-key solutions, yet the best value is typically for a client to developdeeper relationships with their suppliers - thinking of them as a force multiplier, rather than just an outsourcer. Even at amore detailed level, technical security services need to be more integrated, ensuring the smooth inter-relationships betweencomponents like triage, forensics and root cause analysis.Determine what activities should be outsourcedOnce you have reviewed your requirements for cyber security monitoring and logging, you should now determine thetypes of service you require and which of these services you will consider outsourcing to expert suppliers.Many respondents to the Project Survey were willing – to an extent - to consider outsourcing a range of cyber securitymonitoring activities, as shown in the chart below.To what extent would you consider outsourcing the following to providers ofcyber secuity monitoring and logging services?Content filteringThreat intelligence (as opposed to justthreat data or news)Vulnerability management<strong>Security</strong> device management<strong>Cyber</strong> security (protective) monitoringSystem health monitoringBig data analyticsLog retention<strong>Cyber</strong> security incident response0.0 0.5 1.0 1.5 2.02.5 3.0 3.5 4.0 4.5 5.049