Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Cyber-Security-Monitoring-Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
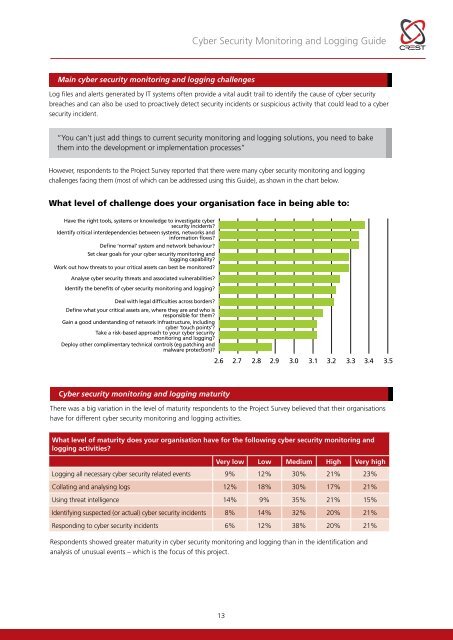
<strong>Cyber</strong> <strong>Security</strong> <strong>Monitoring</strong> and Logging <strong>Guide</strong>Main cyber security monitoring and logging challengesLog files and alerts generated by IT systems often provide a vital audit trail to identify the cause of cyber securitybreaches and can also be used to proactively detect security incidents or suspicious activity that could lead to a cybersecurity incident.“You can’t just add things to current security monitoring and logging solutions, you need to bakethem into the development or implementation processes”However, respondents to the Project Survey reported that there were many cyber security monitoring and loggingchallenges facing them (most of which can be addressed using this <strong>Guide</strong>), as shown in the chart below.What level of challenge does your organisation face in being able to:Have the right tools, systems or knowledge to investigate cybersecurity incidents?Identify critical interdependencies between systems, networks andinformation flows?Define ‘normal’ system and network behaviour?Set clear goals for your cyber security monitoring andlogging capability?Work out how threats to your critical assets can best be monitored?Analyse cyber security threats and associated vulnerabilities?Identify the benefits of cyber security monitoring and logging?Deal with legal difficulties across borders?Define what your critical assets are, where they are and who isresponsible for them?Gain a good understanding of network infrastructure, includingcyber ‘touch points’?Take a risk-based approach to your cyber securitymonitoring and logging?Deploy other complimentary technical controls (eg patching andmalware protection)?2.6 2.7 2.8 2.9 3.03.1 3.2 3.3 3.4 3.5<strong>Cyber</strong> security monitoring and logging maturityThere was a big variation in the level of maturity respondents to the Project Survey believed that their organisationshave for different cyber security monitoring and logging activities.What level of maturity does your organisation have for the following cyber security monitoring andlogging activities?Very low Low Medium High Very highLogging all necessary cyber security related events 9% 12% 30% 21% 23%Collating and analysing logs 12% 18% 30% 17% 21%Using threat intelligence 14% 9% 35% 21% 15%Identifying suspected (or actual) cyber security incidents 8% 14% 32% 20% 21%Responding to cyber security incidents 6% 12% 38% 20% 21%Respondents showed greater maturity in cyber security monitoring and logging than in the identification andanalysis of unusual events – which is the focus of this project.13